Are you worried about an unauthorized account that might be linked to your personal information? We understand how unsettling it can be to discover that someone may have accessed your accounts without your permission. In this article, we'll guide you through the steps you should take to investigate and resolve any potential unauthorized activities. So, grab a cup of coffee and join us as we explore how to protect yourselfâread on for more insights!

Subject Line Clarity
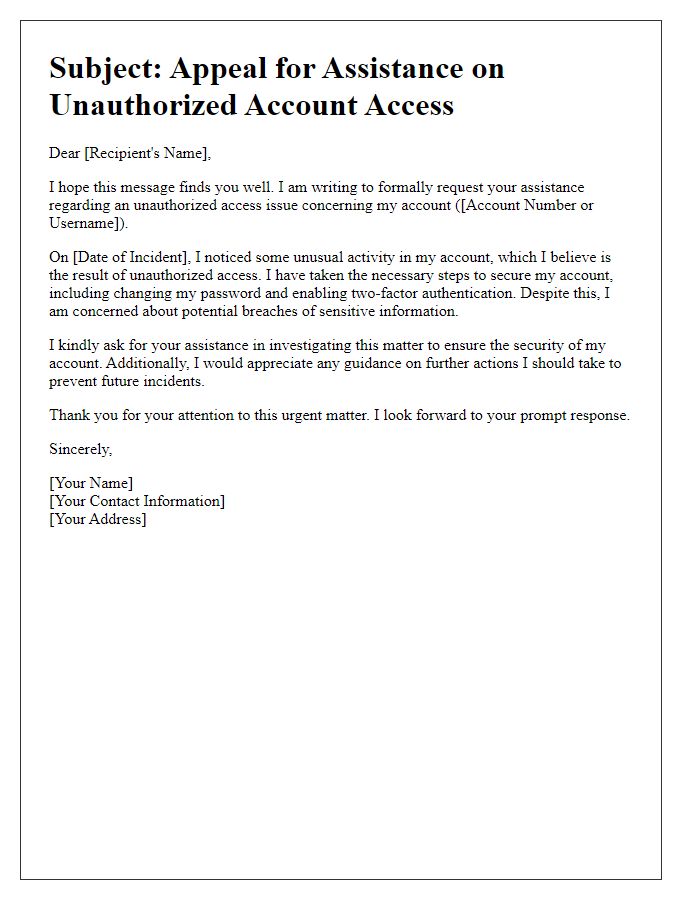
Subject line clarity is crucial when addressing unauthorized account investigations. Clear subject lines, such as "Investigation into Unauthorized Account Activity," immediately inform the recipient of the email's purpose. This specificity ensures efficient routing through customer service channels. Including account identifiers, like account numbers or usernames, facilitates quicker resolution. A concise subject line eliminates confusion, allowing for prompt action. For instance, using "Urgent: Unauthorized Access Detected on Account #123456" conveys urgency and essential details from the outset. Effective subject lines also ensure that the matter gains appropriate attention from the concerned department.
Account Information
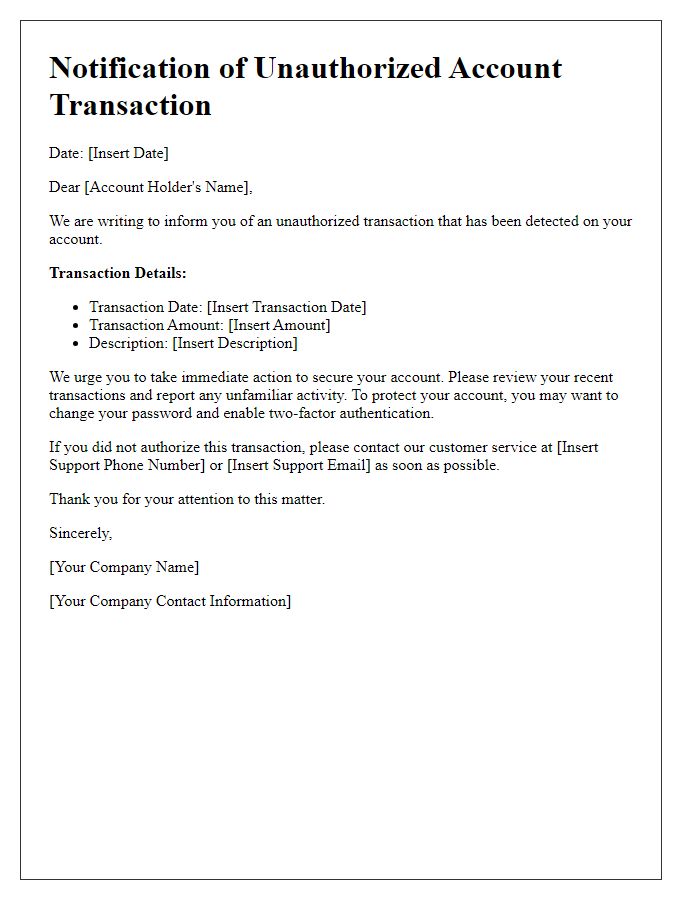
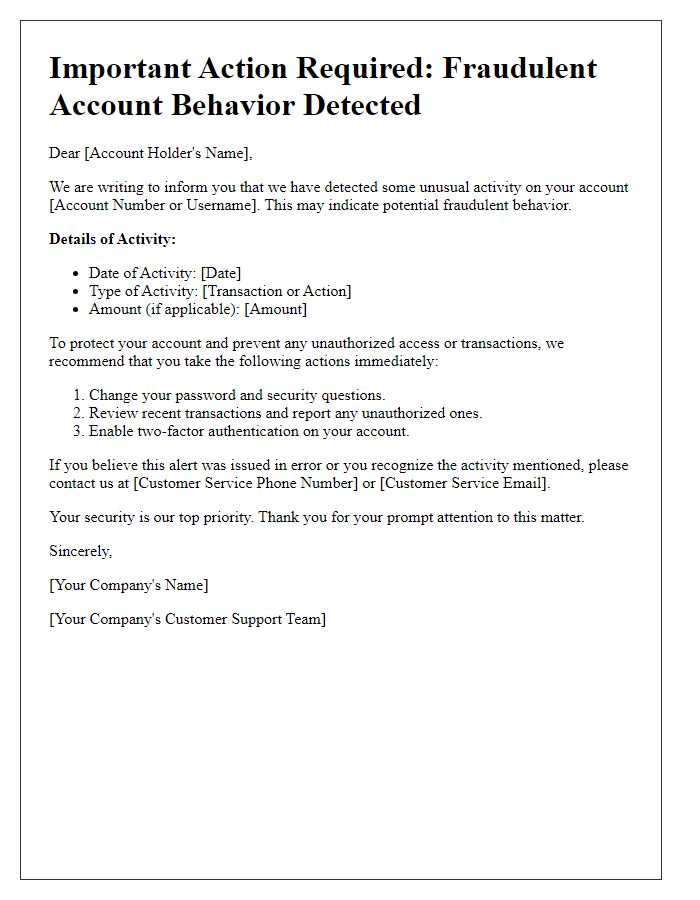
Unauthorized account access can lead to significant security breaches and potential financial loss for users. In cases involving compromised accounts, individuals may notice unusual transactions or changes to personal information such as email addresses or passwords. Institutions, like banks or social media platforms, typically initiate an investigation when alerted by users, focusing on specific account data (like transaction history or login times) to identify unauthorized access patterns. This process often involves verifying user identity through security questions or two-factor authentication and may result in freezing the account to prevent further unauthorized actions. Ultimately, organizations aim to restore user control and enhance security protocols to mitigate future risks.
Incident Description
Unauthorized account access can severely compromise personal security and privacy, necessitating swift action from incident response teams. Investigations often commence upon discovery of suspicious activities, such as unrecognized login attempts originating from unusual IP addresses. For instance, an account may show logged entries from locations like Eastern Europe or Southeast Asia, raising red flags for potential breaches. Security protocols are enacted immediately, including password resets and token verification processes to regain control. Detailed logs, including timestamps and geographic data, are meticulously analyzed, providing insights into the attack vector. User accounts across platforms are monitored for further signs of compromise, influencing decisions on whether to advise affected users and implement additional protective measures. Affected services, such as email providers or social media platforms, often collaborate to issue alerts regarding potential vulnerabilities, emphasizing the importance of robust security practices.
Request for Investigation
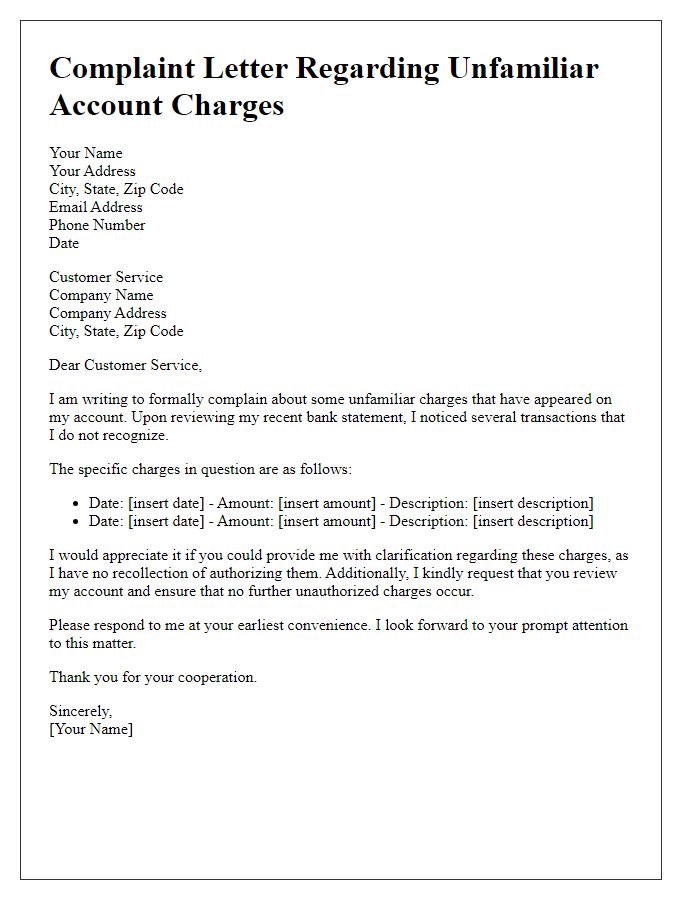
Unauthorized account access can pose significant security risks to individuals and organizations, highlighting the need for prompt investigation. Reports indicate that in 2022, approximately 1.4 million accounts experienced unauthorized access incidents, primarily affecting financial institutions and online services. Locations such as New York and California reported the highest frequency of these breaches, raising concerns about data protection measures in place. Responding swiftly can involve engaging cybersecurity experts and notifying affected users. Key actions include analyzing access logs, identifying suspicious IP addresses, and resetting compromised credentials, ensuring the integrity of the account and protecting sensitive information.
Contact Information
Unauthorized account access can lead to serious privacy breaches and financial losses. Victims often discover suspicious activity when monitoring platforms, such as credit monitoring services like Experian or TransUnion, which provide alerts for unauthorized transactions or changes. Reporting these incidents promptly to authorities like the Federal Trade Commission (FTC) or local law enforcement is crucial. Providing detailed contact information, including a phone number (e.g., 1-877-FTCHelp) and email, can facilitate investigations. Additional steps such as placing fraud alerts on personal credit files with major credit bureaus can further protect affected individuals, minimizing potential damages from identity theft.
Letter Template For Unauthorized Account Investigation Samples
Letter template of request for investigation into suspicious account usage
Letter template of disclosure of potential unauthorized account modifications
Letter template of formal request to suspend an account under investigation





Comments