In today's fast-paced digital world, privacy is more important than ever, and knowing how to manage your information is crucial. Whether you're concerned about personal data or simply wish to have better control over what you share, limiting information sharing is a smart choice. With the right strategies, you can ensure that your private information stays in your hands. So, if you're ready to take charge of your privacy, read on to discover effective tips and templates for limiting information sharing requests!

Purpose Statement
In the rapidly evolving landscape of digital privacy, organizations face increasing pressure to protect sensitive information from unauthorized access. The purpose statement for limiting information sharing requests serves as a critical guideline for institutions aiming to uphold data security and maintain user trust. This statement outlines the framework for minimizing the dissemination of personal data while ensuring compliance with regulations, such as the General Data Protection Regulation (GDPR). By emphasizing the importance of user consent and the need for stringent access controls, organizations can establish a robust policy that prioritizes confidentiality and fosters a secure environment for all stakeholders involved. The implementation of this purpose statement not only protects individual privacy rights but also enhances the overall reputation and integrity of the organization in a competitive marketplace.
Contact Information
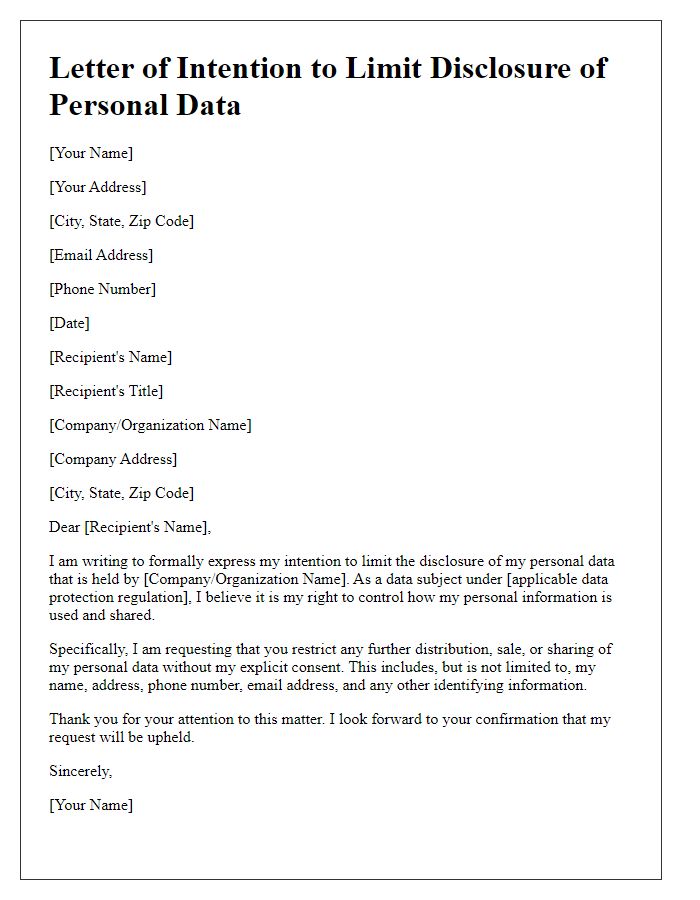
Limiting information sharing requests entail crucial considerations regarding personal data privacy and security. Individuals often seek to restrict the dissemination of sensitive elements like contact information, which includes names, email addresses, phone numbers, and mailing addresses. This request can originate from various entities, such as consumers, employees, or members of organizations. Regulatory frameworks like the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) outline the rights individuals have regarding their personal data. In practice, when limiting information sharing requests are made, organizations must examine their data handling practices, ensuring compliance to prevent unauthorized access and potential data breaches, which can have severe repercussions like identity theft or financial fraud.
Specific Information to Limit
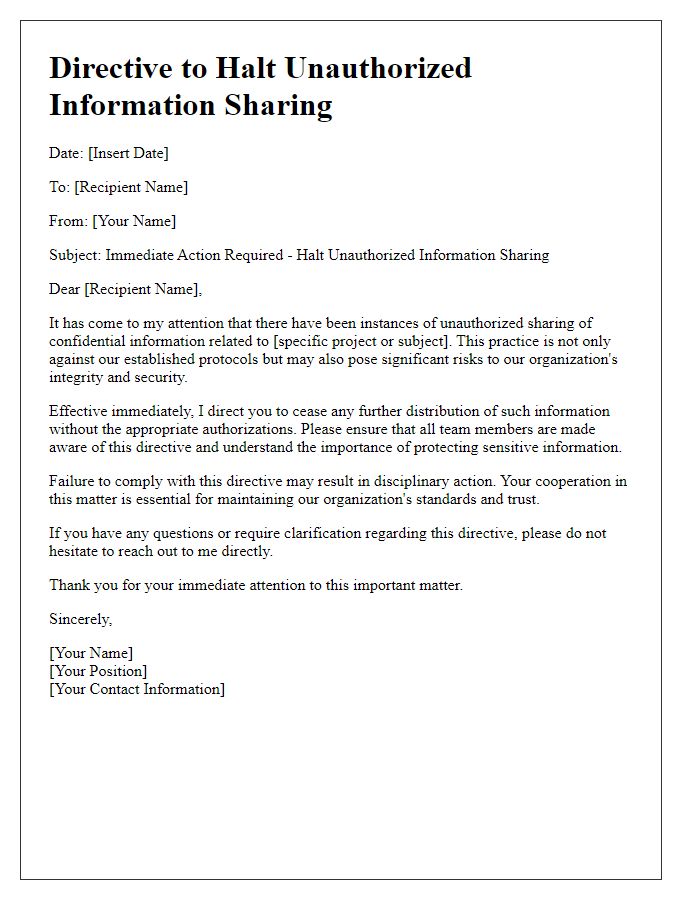
A limiting information sharing request can be essential in protecting sensitive data. For instance, personal identifiers (such as Social Security Numbers, medical records, and financial data) should be scrutinized when shared with third parties, particularly in sectors like healthcare, finance, and education. Additionally, limiting the sharing of proprietary business information (such as trade secrets, client lists, and strategic plans) can prevent competitive disadvantage and data breaches. Data privacy regulations (like GDPR in Europe or CCPA in California) emphasize the necessity for organizations to have clear, stringent policies regarding what information can be disclosed. By doing so, companies can safeguard proprietary information in an increasingly digital landscape.
Justification for Limitation
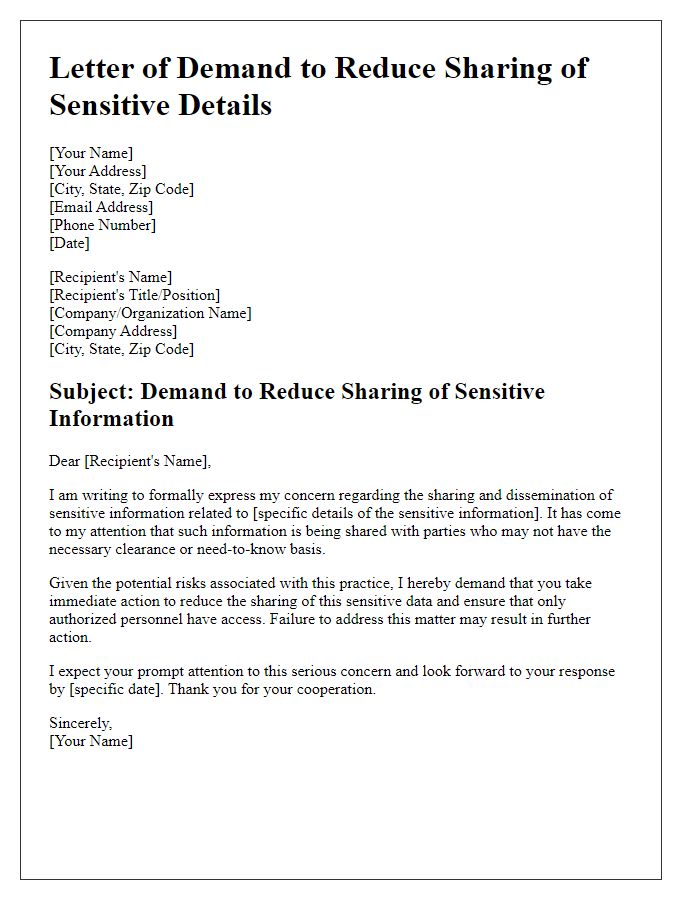
Companies often face requests for limiting information sharing based on privacy concerns or regulatory compliance. The General Data Protection Regulation (GDPR) emphasizes individuals' rights to control their personal data. Legitimate reasons for limiting information sharing may include safeguarding sensitive data, such as financial records or health information, which if disclosed, could lead to identity theft or discrimination. Another justification can be protecting proprietary business information, like trade secrets or client lists, which are crucial for maintaining competitive advantage. In contexts such as government institutions, national security risks may necessitate limiting information dissemination to prevent unauthorized access to classified materials. Organizations must carefully evaluate these justifications to ensure legal and ethical standards are upheld while managing information responsibly.
Request for Confirmation and Follow-Up
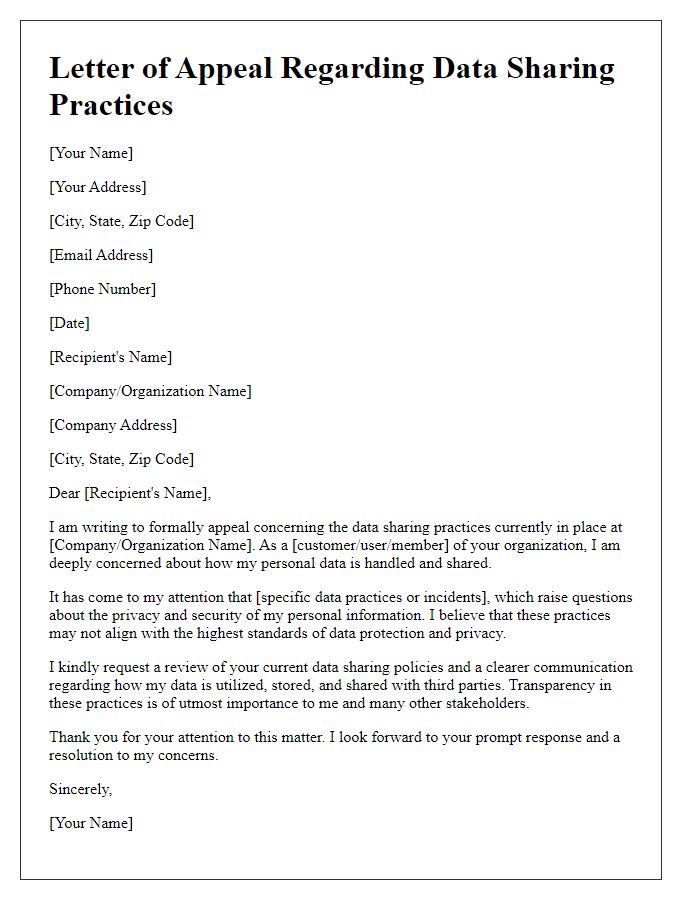
In today's digital landscape, safeguarding personal data has become increasingly important, especially in corporate environments. The implementation of data protection laws, such as the General Data Protection Regulation (GDPR) enacted in May 2018, underscores the necessity of controlling how personal information is shared with third parties. Companies must proactively communicate with stakeholders, ensuring they confirm what information will be shared and with whom. Such confirmation could involve details like the specific nature of the data, the purpose for which it is shared, and the entity receiving the information--be it a partner organization in the healthcare sector or a marketing firm. Following up with an additional request for verification not only reinforces compliance practices but enhances trust between the organization and the individuals whose data is being handled.
Letter Template For Limiting Information Sharing Request Samples
Letter template of inquiry to curtail private information dissemination.



Comments