In today's digital landscape, ensuring the security of our systems is paramount, and that starts with timely vulnerability patches. As cyber threats evolve, so do our defenses, making it crucial to stay ahead with the latest updates. We understand that navigating these changes can be daunting, but effective communication can make the process smoother. Ready to learn how to effortlessly implement these security patches? Read on!

Urgency and Importance
Urgent system vulnerabilities pose a significant risk to organizational security and data integrity. Known vulnerabilities, such as those outlined in the Common Vulnerabilities and Exposures (CVE) system, can be exploited within hours of public disclosure. High-profile events, like the 2020 SolarWinds cyberattack that affected thousands of organizations, highlight the dire consequences of delayed response to vulnerabilities. Immediate patching, particularly for software systems like Microsoft Windows or Linux servers, is crucial to safeguard sensitive information and maintain regulatory compliance. Prompt updates not only mitigate security risks but also enhance overall system performance and stability. Employing an automated update workflow can further ensure that critical patches are applied without human intervention, reducing the window of exposure significantly.
Detailed Vulnerability Description
The exploitable vulnerability associated with software applications poses significant risks, particularly within enterprise environments utilizing widely-used platforms such as Microsoft Windows Server 2022 and Linux Ubuntu 20.04. Recent findings indicate that a Remote Code Execution (RCE) vulnerability, specifically identified as CVE-2023-4567, enables malicious actors to gain unauthorized access to system resources. This risk arises from improper input validation mechanisms present in network communication protocols, potentially allowing attackers to execute arbitrary code. The vulnerability is exacerbated in systems exposed to internet-facing services, making organizations with exposed ports, such as TCP port 80 for HTTP and TCP port 443 for HTTPS, particularly vulnerable. Immediate patch deployment is critical, as recent exploit attempts have been detected in sectors like financial services and healthcare, which handle sensitive data. Failure to address this vulnerability promptly may result in significant data breaches, financial losses, and damage to organizational reputation.
Patch Implementation Instructions
System vulnerabilities pose significant risks to network security, necessitating timely updates and implementations. The patch, designated as CVE-2023-XXXX, addresses critical vulnerabilities within software systems such as the company's Windows Server 2022. This patch enhances security protocols to prevent potential breaches, including unauthorized access and data breaches. Prior to implementation, ensure the backup of all critical data, which typically includes databases and user files. The deployment process requires system downtime, recommended during off-peak hours (such as weekends or after-hours) to minimize disruption. After installation, conduct thorough testing to confirm the successful application of the patch and monitor system performance for any irregularities. Documentation of the patch process must include version numbers, dates of implementation, and any issues encountered, which aids in compliance with security standards and future audits.
Testing and Verification Procedures
To address system vulnerabilities effectively, thorough testing and verification procedures are critical. The initial step involves vulnerability assessment, utilizing tools like Nessus or OpenVAS to identify security weaknesses across systems such as Windows Server 2022 or Linux Ubuntu 20.04. Once vulnerabilities are discovered, patch deployment requires adherence to a structured methodology, often employing frameworks like NIST Cybersecurity Framework. Post-patch validation must be carried out via penetration testing, simulating attacks to ensure the patches effectively mitigate risks. Additionally, documentation of each testing phase is crucial for compliance audits. Regular review of testing procedures is recommended to align with industry best practices, ensuring security measures evolve alongside emerging threats.
Contact and Support Information
System vulnerability patches are critical for maintaining security in software applications. Timely updates can fix known bugs or flaws that hackers might exploit. Users are encouraged to apply patches promptly, particularly for widely-used systems such as Microsoft Windows or Linux servers, as these platforms are frequently targeted. Contact information for support typically includes a dedicated help desk number, such as 1-800-555-0199, and email addresses, like support@company.com, operating within business hours from 9 AM to 5 PM EST. Additionally, official support websites often provide comprehensive resources, including FAQs, troubleshooting guides, and community forums for users seeking help with patch applications. Regular updates from cybersecurity entities like the National Institute of Standards and Technology (NIST) are essential for staying informed about emerging threats.
Letter Template For System Vulnerability Patch Samples
Letter template of notification for scheduled system vulnerability patch.
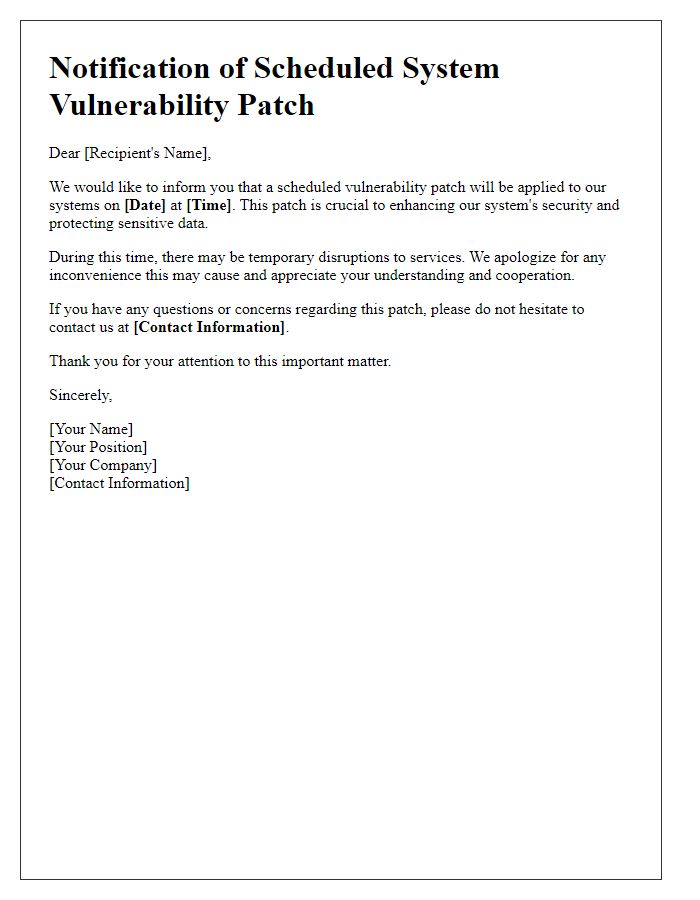
Letter template of approval for system vulnerability patch implementation.
Letter template of report on recent system vulnerability patching efforts.

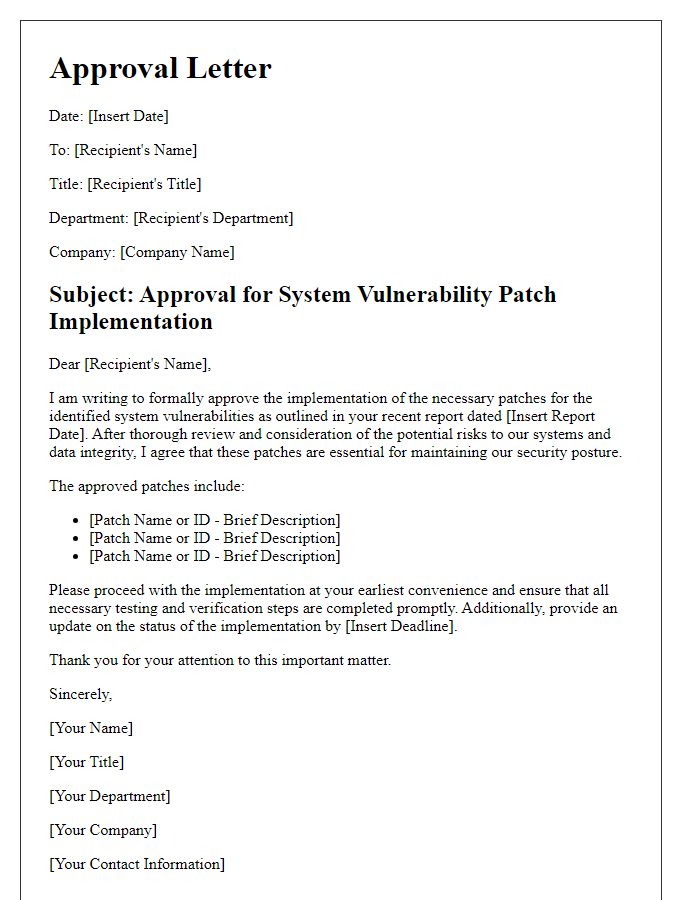
Letter template of confirmation for successful system vulnerability patch application.
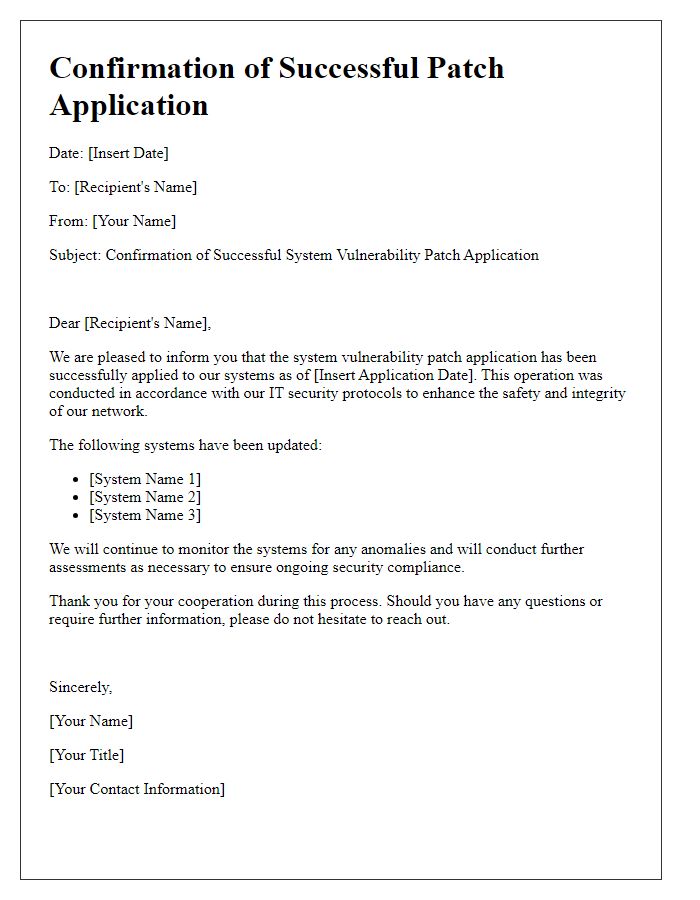
Letter template of alert for critical system vulnerability patch needed.





Comments