Are you looking to streamline the process of granting temporary access credentials for your team or clients? In today's fast-paced digital world, ensuring that access is both secure and efficient is more important than ever. This guide will provide you with a user-friendly letter template that simplifies the process, ensuring clarity and professionalism. So, let's dive in and explore the best practices for crafting your temporary access credential letters!

Recipient's contact information
Temporary access credentials are essential for secure entry into restricted systems or environments, such as corporate networks or proprietary databases. Unauthorized access attempts can jeopardize sensitive data, including Personal Identifiable Information (PII) and financial records. Properly formatted credentials, containing alphanumeric character combinations, ensure that only authorized individuals gain access within stipulated time frames. Always include the recipient's contact information, which may encompass their full name, job title, email address, and phone number, to confirm identity and facilitate communication. It's crucial that these credentials are unique and time-sensitive, generally expiring after a specified duration, often around 30 days, to enhance security.
Purpose of access
Temporary access credentials enable users to perform specific tasks within secure systems or networks, particularly during periods requiring limited resource availability. For instance, temporary login credentials may provide access to sensitive data for project collaborations, troubleshooting efforts, or emergency maintenance. These credentials are often time-bound, typically expiring within 24 hours to 30 days, depending on the organization's security protocols. To maintain cybersecurity, organizations implement stringent controls, including audit logs that track access times and user activities. Enhanced verification methods, such as two-factor authentication, ensure that only authorized personnel can utilize these credentials, thus safeguarding the integrity of sensitive information.
Credential details (username/password)
Temporary access credentials for restricted systems must be managed with care. Username and password combinations serve as essential gateways to sensitive data. For instance, a username might typically reflect the employee's ID number, such as "emp1234," while the password is often a complex string, including uppercase letters, lowercase letters, numbers, and special characters, like "P@ssw0rd!". These credentials should be valid for a limited period--commonly ranging from 24 hours to 7 days--to ensure security. Access logs must be monitored to audit usage during this temporary period, and these credentials should be deactivated immediately after the specified time limit, or upon completion of tasks.
Duration of access validity
Temporary access credentials are crucial for maintaining security while permitting limited access to systems or facilities. The access validity period typically spans from 24 hours to several weeks, depending on the specific requirements of a project or task. For example, contractors may receive credentials valid for 14 days to complete their assignments at the corporate office located at 123 Business Lane, New York. This structured timeframe ensures that unauthorized access is minimized once the project concludes. Each credential, often embedded with an expiration timestamp, automatically disables access upon reaching the designated duration, enhancing overall security protocols within the organization.
Security instructions and guidelines
Temporary access credentials should be issued carefully to ensure safety and security. Each credential should have a unique identifier, valid for a specific period, and include details such as the user's name, purpose of access, and expiration date. Adherence to security protocols, including verification of the user's identity through two-factor authentication methods (like SMS or email codes), is crucial. Access should be restricted to specific areas, governed by the principle of least privilege, meaning individuals receive only the access necessary for their tasks. Regular auditing of temporary access records, especially for sensitive locations like data centers or secure labs, must be conducted to detect unauthorized use. Provide detailed instructions on how to securely store and return temporary credentials after use, reinforcing the importance of confidentiality and data protection compliance.
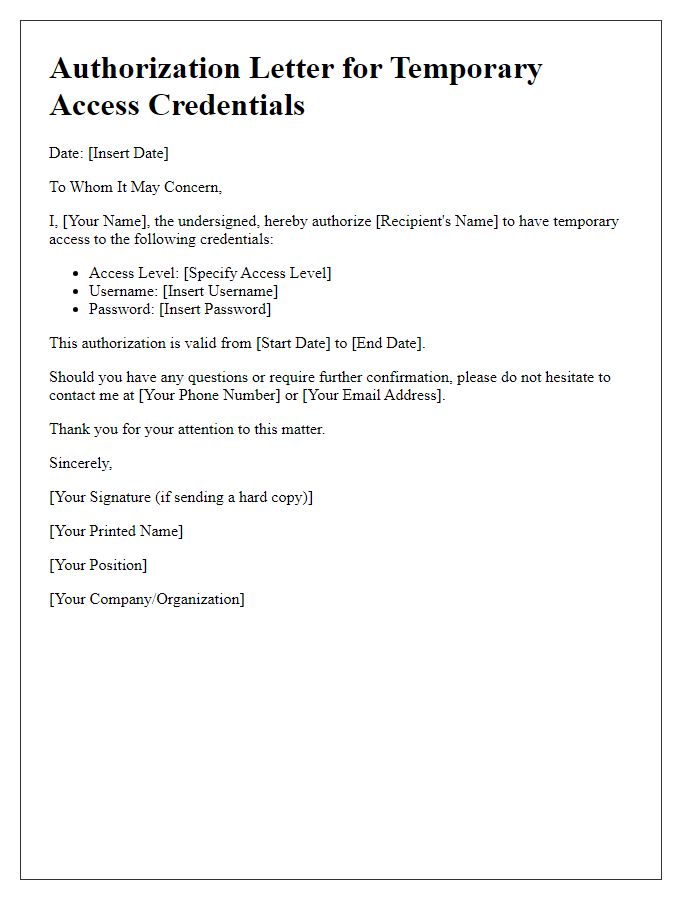
Letter Template For Temporary Access Credentials Samples
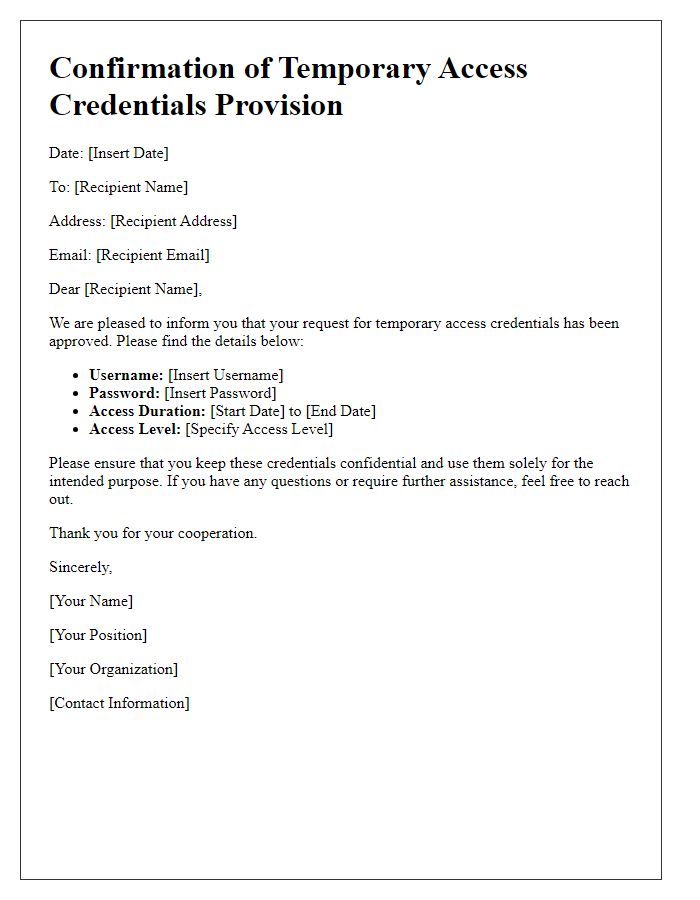
Letter template of confirmation for temporary access credentials provision
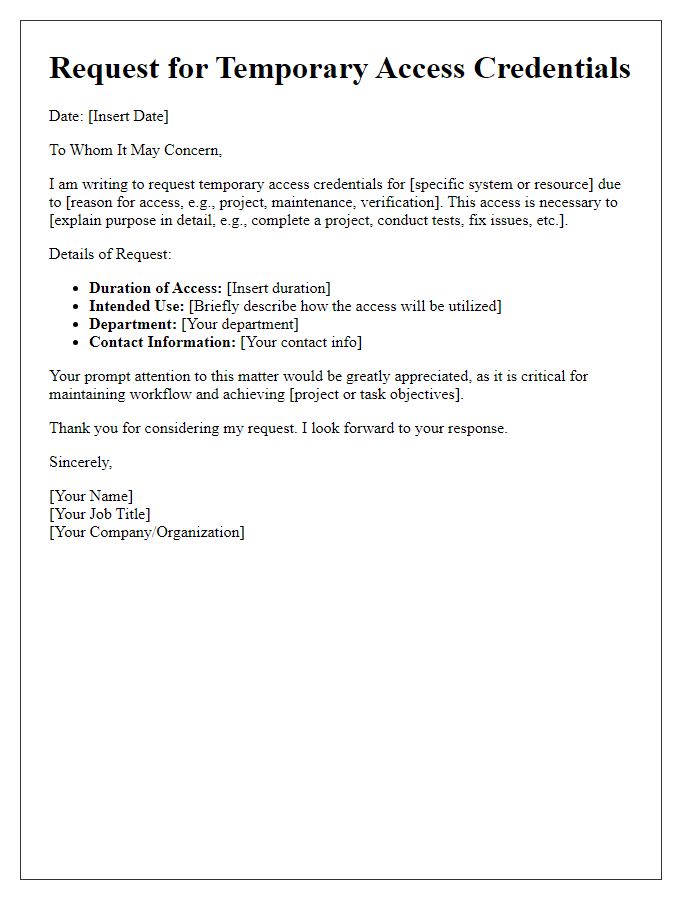
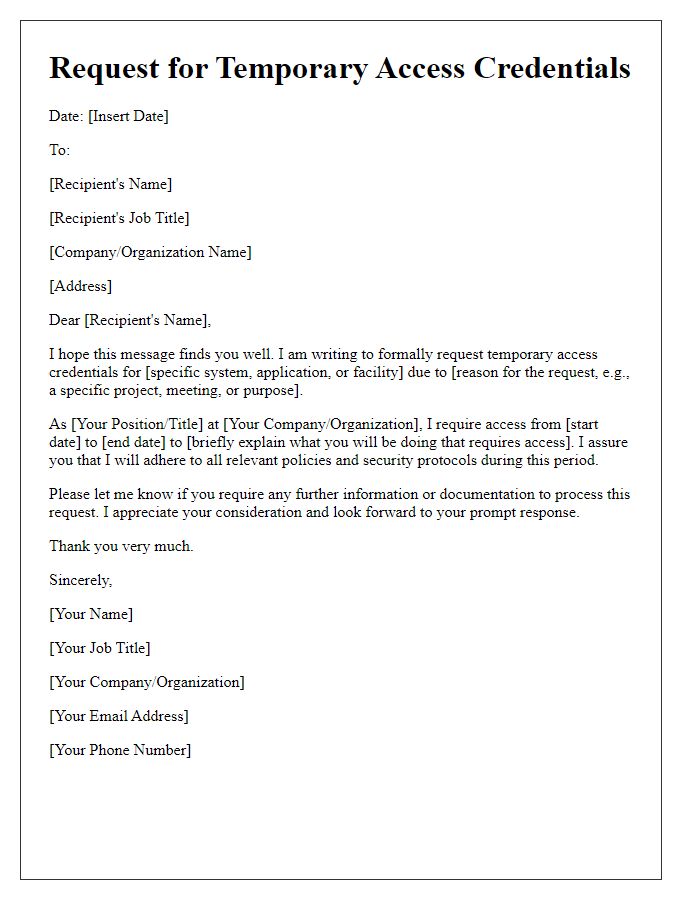
Letter template of justification for needing temporary access credentials




Comments