Are you looking for a straightforward way to confirm access authorization? Whether you need to provide a secure connection for employees, contractors, or clients, a well-crafted letter can help facilitate that process. In this article, we'll guide you through the essential elements of a confirmation letter that not only conveys clear information but also reinforces your commitment to security. So, let's dive in and explore how to create an effective access authorization letter!

Personalized Greeting
Access authorization confirmation is crucial in maintaining security protocols for sensitive environments, such as corporate offices or data centers. This authorization typically involves a specific individual, identified by name and title, granted access to designated areas or systems. The confirmation process often includes issuance of access badges or keycards, often embedded with technology such as RFID (Radio Frequency Identification). Such authorizations may also be limited to specific times and dates (for example, weekdays between 9 AM and 5 PM), ensuring controlled entry. Additionally, records of access are maintained for auditing purposes, contributing to organizational oversight and compliance with regulations like GDPR (General Data Protection Regulation) in Europe.
Clear Access Details
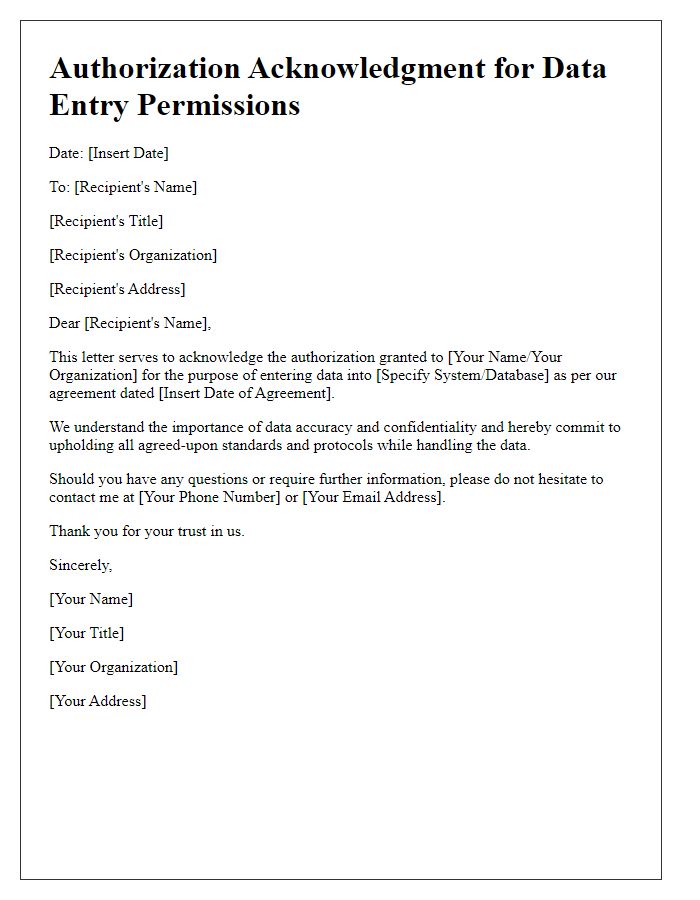
Access authorization confirmation outlines the permissions granted to individuals or entities regarding sensitive areas or information. The confirmation document specifies the identity of the authorized personnel, such as employee ID or organization name, along with the detailed parameters of access, including locations (e.g., restricted areas within a building, secure server rooms), duration (e.g., specific dates or ongoing until revoked), and any limitations on the type of access (such as electronic versus physical entry). Additionally, the document may include references to compliance policies or security protocols, highlighting the importance of responsible handling of sensitive information and adherence to protocols established by governing bodies or organizational policies, like ISO 27001. Proper documentation ensures accountability and traceability of access, mitigating risks related to unauthorized access.
Effective Date and Duration
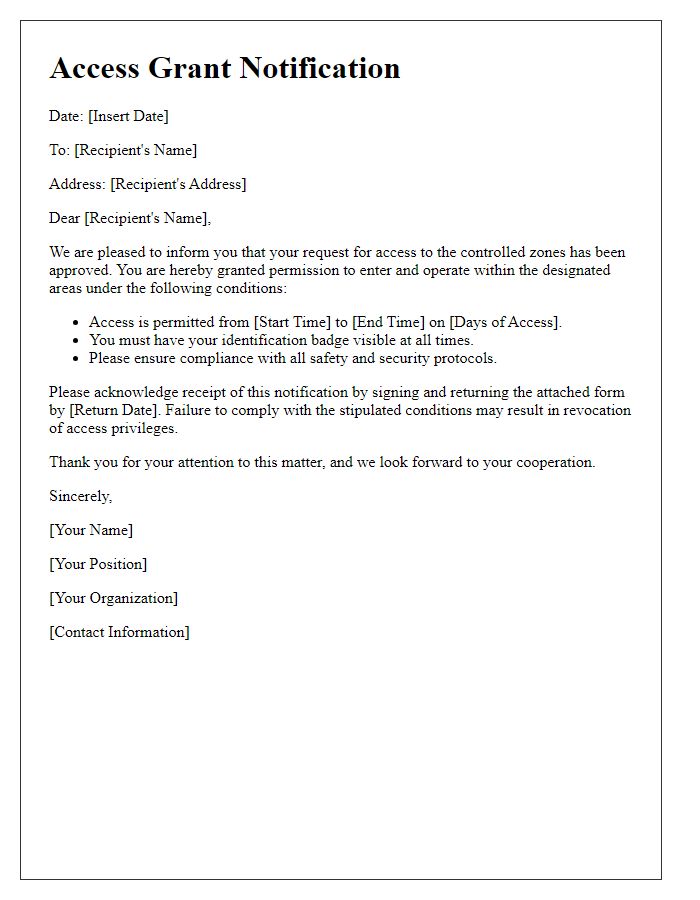
Access authorization confirms the right to enter specific areas or use certain resources within an organization, essential for security management. The effective date signifies the moment when access privileges commence, typically noted as the date of approval or documentation (e.g., April 1, 2023). The duration defines how long these privileges remain valid, which can range from a specified period (e.g., six months) to ongoing access until revoked. Maintaining updated records of access authorization is crucial for monitoring compliance and ensuring the safety of sensitive information and restricted areas, such as data centers or laboratories.
Security and Compliance Guidelines
Access authorization for sensitive locations within corporate environments adheres strictly to Security and Compliance Guidelines as established by organizations such as ISO 27001. Detailed procedures ensure that only individuals with verified credentials can enter secure premises, safeguarding assets against unauthorized access. Access control systems (like key card readers and biometric scanners) maintain logs of entry and exit times for auditing purposes. Regular compliance audits, conducted every six months, assess adherence to these protocols, highlighting the importance of protecting data and maintaining the integrity of security measures. Ensuring that all personnel are trained on these guidelines and understand their responsibilities is vital for mitigating risks associated with data breaches and ensuring organizational security.
Contact Information for Inquiries
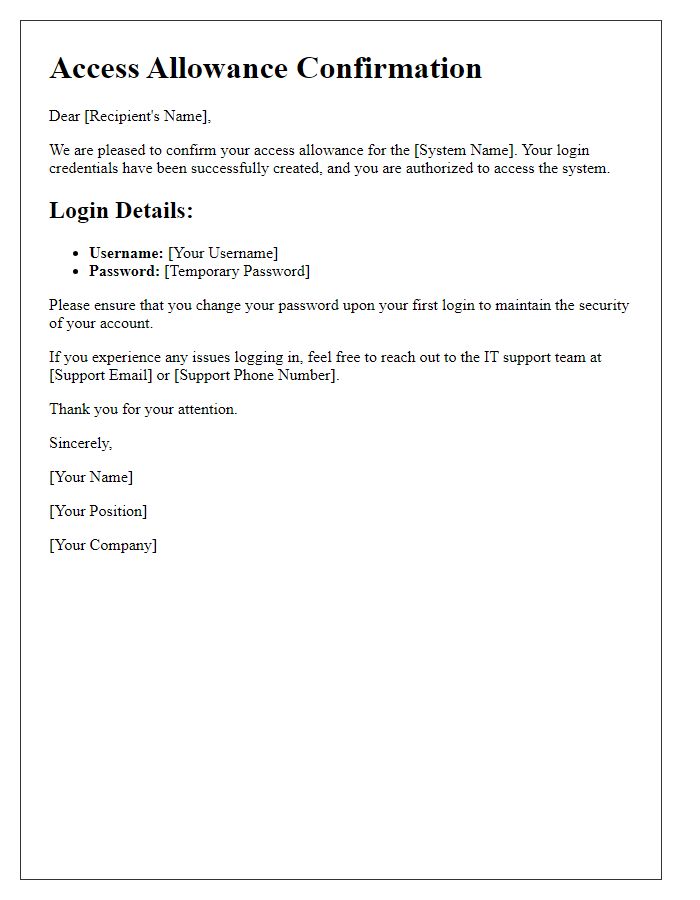
Authorization access confirmation serves as a vital document in various organizational settings. It typically includes specific details such as the name of the individual granted access, date of authorization issuance, and the areas within the facility--involving sensitive information or secure locations--that are now accessible. This confirmation may also encompass a unique authorization number that helps streamline tracking and auditing processes within the organization. Furthermore, there should be a clear mention of the duration for which access is granted, often tying it to particular projects, events, or time frames, to ensure compliance with security protocols. Contact information for inquiries must be provided, including email addresses and phone numbers of designated personnel responsible for overseeing access control and addressing any queries or concerns regarding the authorization. This structured approach maintains security integrity while ensuring clarity in communication.
Letter Template For Confirmation Of Access Authorization Samples
Letter template of access clearance verification for confidential locations

Letter template of access credential validation for sensitive environments





Comments