In today's fast-paced digital world, effectively managing your assets can make all the difference in your business operations. A well-structured authorization letter not only streamlines the process but also ensures everyone is on the same page regarding digital asset handling. Crafting the perfect digital asset management authorization letter is essential for maintaining organization and security. Curious to learn how to create an impactful authorization letter? Read on for our comprehensive guide!

Clear identification of parties involved
Clear identification of parties involved in digital asset management is essential for establishing accountability and clarity. The primary entity, the Asset Owner (e.g., a company like ABC Corp), holds ownership rights over the digital assets, including files, images, and videos, crucial for branding and marketing strategies. The Authorized User (e.g., Jane Doe, Marketing Manager) is designated to access, edit, and distribute those assets according to established guidelines. Additionally, third-party vendors, such as XYZ Agency, might be included in the authorization process for collaborative projects. Such clear identification ensures proper access control and maintains the integrity of the digital asset management system, streamlining workflows within companies and safeguarding against unauthorized use.
Detailed scope of authorization
Digital asset management (DAM) systems play a crucial role in organizing, storing, and controlling access to digital assets such as images, videos, and documents. The authorization process defines the permissions granted to users within the DAM system, specifying roles such as administrator, editor, and viewer. Users with administrator access (typically limited to two or three individuals) have the authority to modify metadata, manage user accounts, and implement security protocols. Editors, who may comprise a larger group (up to 15 users), possess permissions to upload, edit, and delete assets, ensuring content remains current and relevant. Viewers, representing the broadest audience (potentially hundreds, including stakeholders from various departments), are granted access to browse the digital library without alteration capabilities. This structured hierarchy ensures that sensitive digital assets are protected, facilitating effective collaboration while maintaining stringent security measures across the organization.
Comprehensive list of digital assets
A comprehensive list of digital assets is essential for organized digital asset management. These assets include high-resolution images, typically stored in JPEG or PNG formats, which serve branding purposes on websites and social media platforms. Videos, often in MP4 format, used for marketing campaigns or educational content, are critical for engaging audiences. Audio files, such as MP3 tracks, provide background music for videos or podcasts, enhancing user experience. Furthermore, documents in PDF format, including reports and brochures, are vital for distributing important information across platforms. Metadata elements, like keywords and descriptions, enhance searchability and accessibility of these digital assets across digital libraries or asset management systems. Regular audits (at least annually) of these assets ensure relevance and compliance with copyright regulations, assisting in maintaining brand integrity and legal standing.
Duration and terms of authorization
Digital asset management (DAM) involves the systematic organization and distribution of digital assets, including images, videos, documents, and audio files. A well-defined duration for authorization is crucial, often ranging between six months to two years, depending on the organizational needs and project timelines. Terms of authorization typically stipulate user permissions, access levels, and conditions under which access can be granted or revoked; compliance with copyright laws, confidentiality, and content usage rights may also be integral. Clear documentation ensures accountability, fostering a structured approach to managing digital resources efficiently. Organizations utilizing cloud-based DAM solutions, like Adobe Experience Manager or Widen Collective, often require adherence to specific service-level agreements (SLAs).
Security and confidentiality measures
Digital asset management (DAM) authorization is essential for ensuring robust security and confidentiality of sensitive digital content. Organizations often employ measures such as encryption (high-level algorithms like AES-256) to protect assets during storage and transmission. Access controls, including role-based permissions, limit viewing rights to authorized personnel only, significantly mitigating data breaches. Audit trails record user interactions with assets, enhancing transparency and accountability. Regular security assessments, compliance with standards like ISO 27001, and training for employees on data handling best practices further solidify the security framework. Implementing secure backup procedures ensures asset recovery in case of cyber incidents, protecting organizational integrity.
Letter Template For Digital Asset Management Authorization Samples
Letter template of digital asset management authorization for individual use.

Letter template of digital asset management authorization for team collaboration.
Letter template of digital asset management authorization for company-wide access.

Letter template of digital asset management authorization for third-party vendor access.

Letter template of digital asset management authorization for project-specific resources.
Letter template of digital asset management authorization for limited-time usage.
Letter template of digital asset management authorization for subscription-based services.
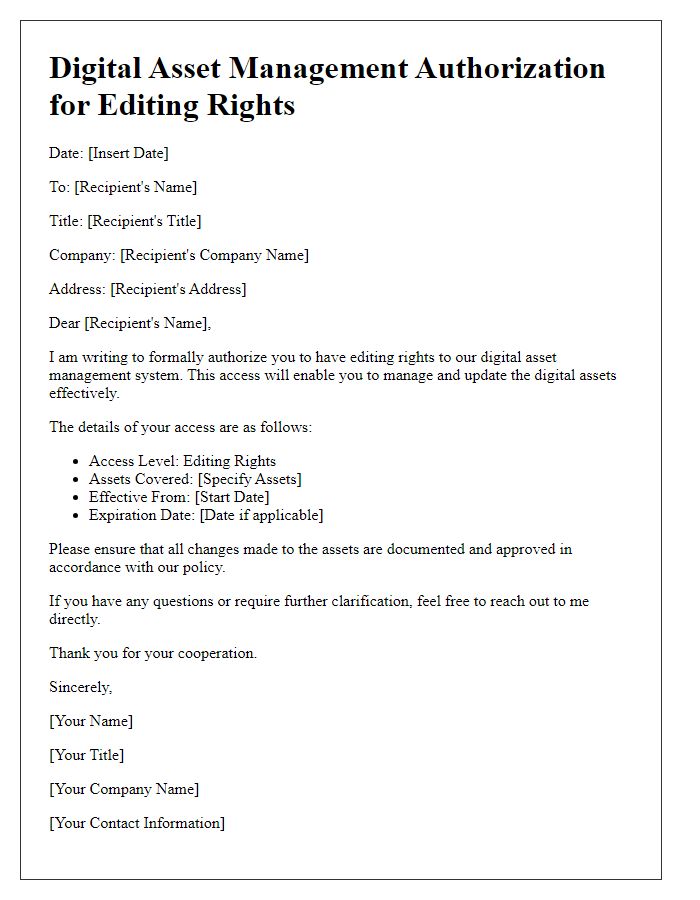
Letter template of digital asset management authorization for editing rights.
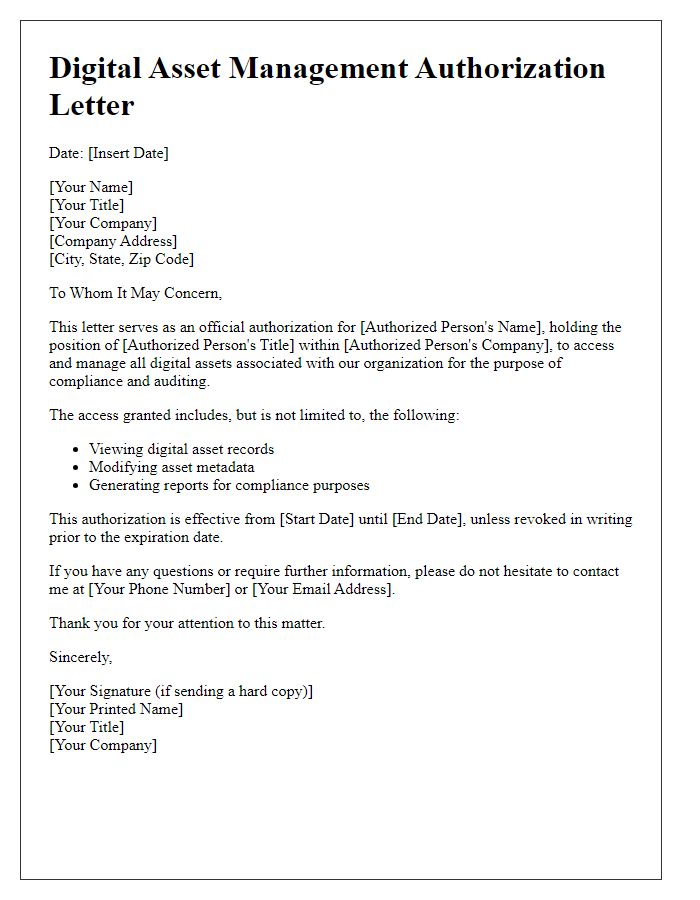
Letter template of digital asset management authorization for data retrieval.




Comments