Are you looking to confirm system access in a clear and professional manner? Writing a letter that succinctly conveys the necessary information can make a significant difference in your communication. In this article, we'll provide you with a versatile letter template that ensures all essential details are included while maintaining a friendly tone. So, let's dive in and explore how to structure your confirmation of system access letter!

Employee Information
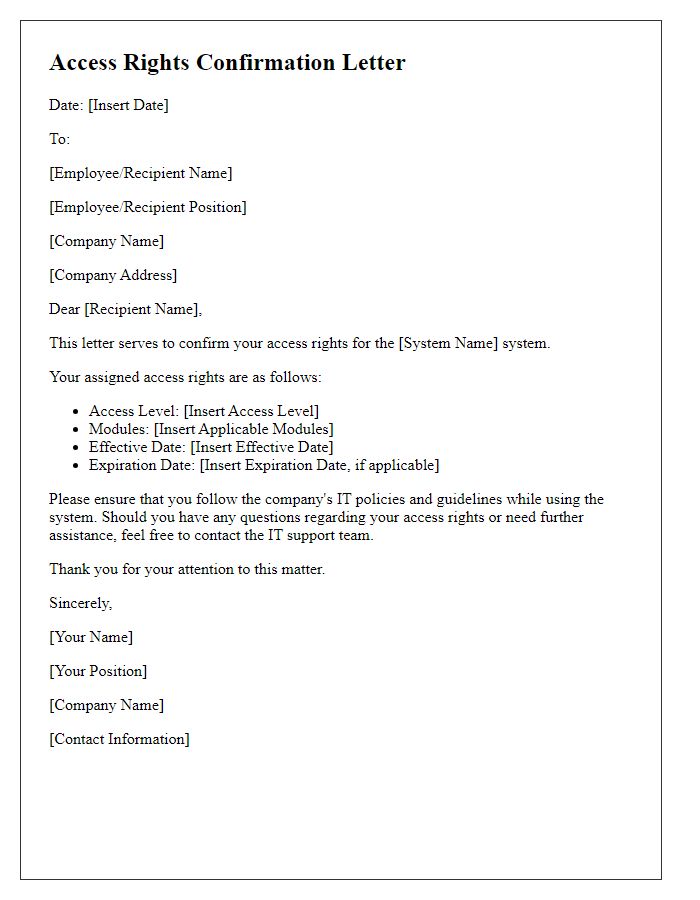
System access confirmation is crucial for maintaining security within the company infrastructure. Employee profiles include essential details such as employment ID, role designation, and department assignment. The Human Resources department monitors system access privileges to ensure alignment with job responsibilities, minimizing unauthorized access risks. Verification process typically involves the IT department, which enforces access controls based on proactive security measures and compliance with company policies. Regular audits occur quarterly to assess and update access permissions, safeguarding sensitive information against potential breaches. Security training is mandatory for all employees, reinforcing the importance of data protection protocols within the organization.
Access Level and System Details
The confirmation of system access ensures that users understand their permissions and the nature of the system they can access. It may include specific access levels, such as Administrative, User, or Read-Only, which determine the extent of their privileges within the system. Additionally, system details should encompass the system's name, such as "Corporate Intranet," its purpose (e.g., facilitating internal communication and data sharing), and the platform type (e.g., cloud-based or on-premises). Security measures, such as multi-factor authentication and encryption protocols, are critical to maintaining data integrity and protecting sensitive information. Clear documentation enhances user awareness and compliance with security policies.
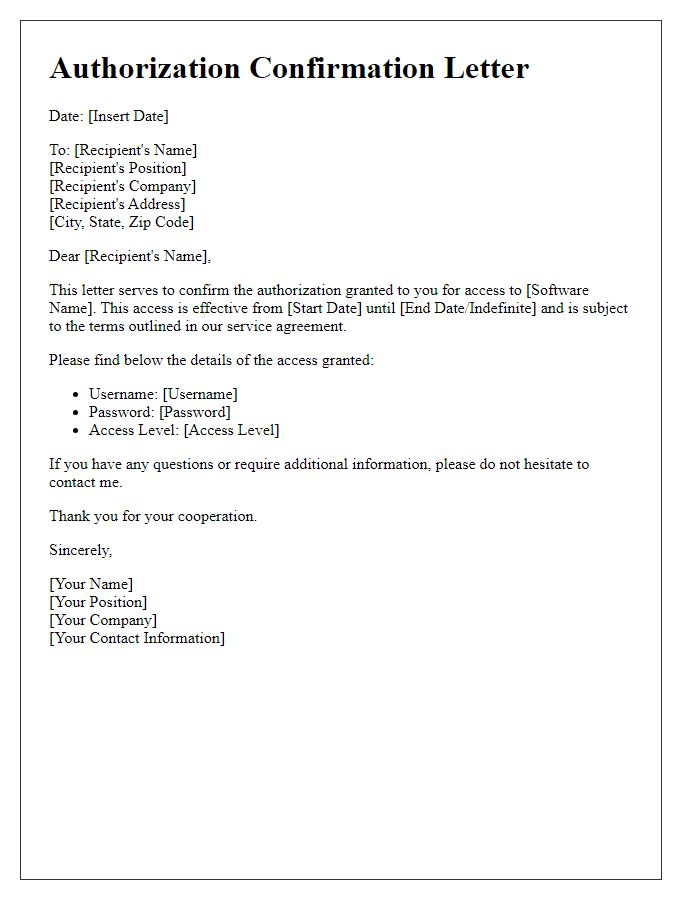
Authorization and Approval
Access confirmation for systems requires careful documentation indicating authorization and approval. Security protocols in organizations often mandate that access to sensitive information systems, such as financial databases or customer relationship management (CRM) tools, be clearly outlined. Documentation, typically generated via internal IT departments, details the individuals granted access, alongside their roles, permissions, and the date of approval. This approach helps ensure compliance with regulatory standards like GDPR or HIPAA, particularly for organizations that handle private data. Further, audit trails enabled by system logs play a crucial role in monitoring access, providing a record of user activities, and enhancing overall cybersecurity measures.
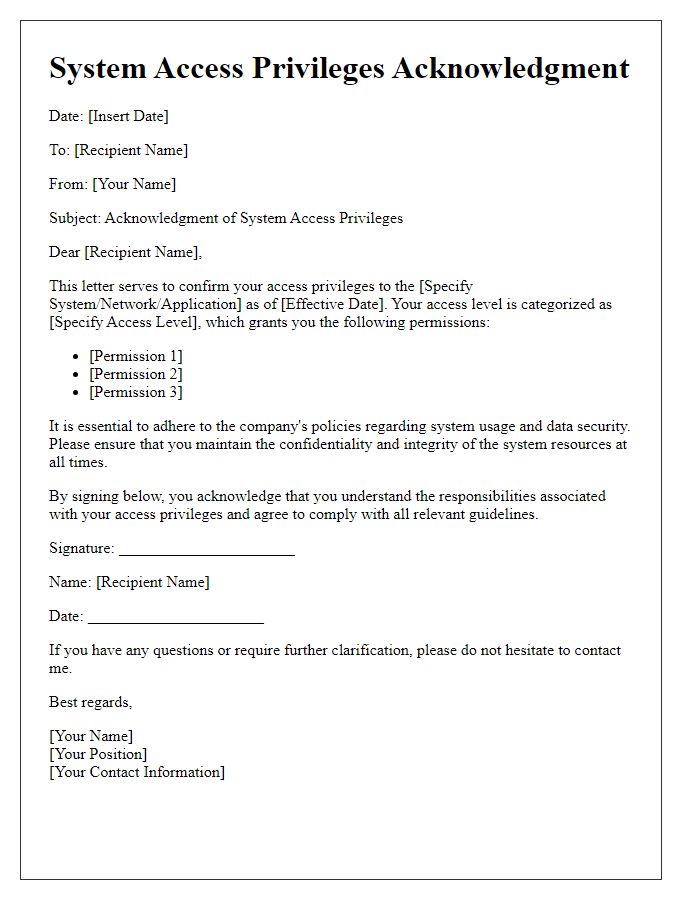
Security and Compliance Guidelines
Access to secure systems must adhere to stringent Security and Compliance Guidelines outlined by the organization. Employees granted access are expected to follow protocols to protect sensitive data located within these systems, such as customer information (personal identification numbers, addresses, account details) and intellectual property (trade secrets, product specifications). Regular training sessions on compliance practices, including data encryption methods and incident response procedures, should be attended to ensure awareness of risks. Unauthorized access attempts may result in disciplinary action, including removal of access privileges and potential legal implications. Annual audits, conducted by the Compliance Department, verify adherence to guidelines and assess security measures in place to prevent data breaches.
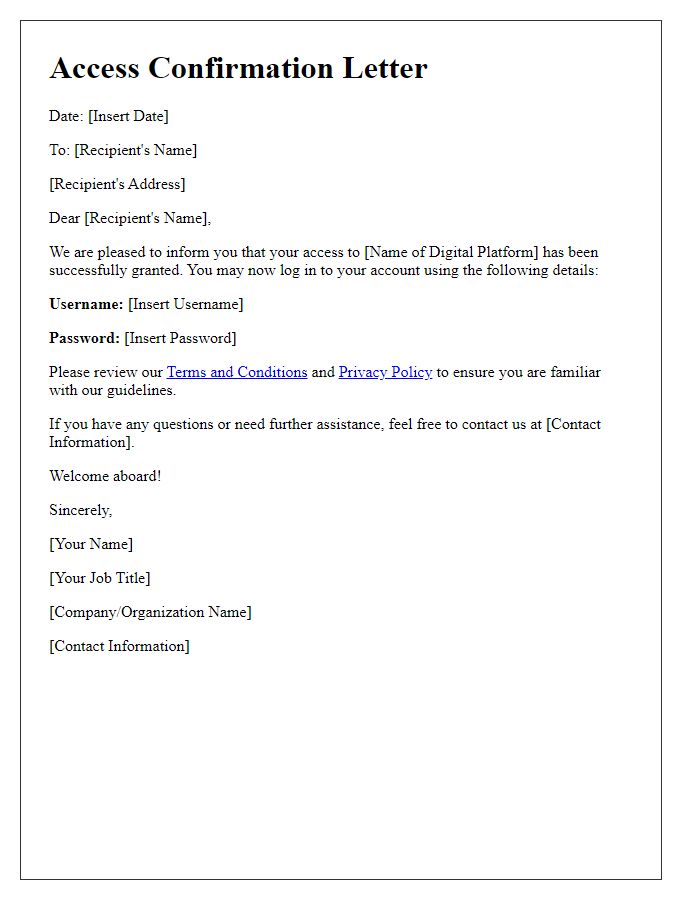
Contact Information for Support
Access to secure systems at the organization is contingent upon successful verification of user credentials. A valid email address (for instance, john.doe@example.com) and contact number (+1-555-123-4567) are essential for support communication. Should you encounter any issues, our IT support team is available 24/7. Access to critical data and applications relies on confirming user identity, involving unique identifiers such as employee ID (e.g., 987654) and secure access tokens. Ensure your login information is safeguarded to maintain data integrity.




Comments