Are you looking to create a letter that grants a beneficiary restricted access authorization? It's important to ensure that your document is clear and effectively communicates the necessary permissions while protecting sensitive information. Writing such a letter doesn't have to be complicated; with the right template, you can easily outline the specific access rights granted to the beneficiary. Dive into this article to discover an easy-to-follow letter template that will simplify the process for you!

Clear Identification of Parties
Beneficiary restricted access authorization outlines the clear identification of parties involved in financial transactions or agreements. This authorization typically involves the account holder (beneficiary), often an individual or organization, and the institution or financial entity responsible for managing the account. It's crucial to provide detailed identification such as full legal names, account numbers, and contact information to ensure accurate recognition and facilitate proper access permissions. The clear delineation of roles--who is granting access and who is receiving it--supports compliance and minimizes the risk of unauthorized transactions. Additionally, including the date and purpose of the authorization strengthens the document's legitimacy and provides a basis for any potential future disputes.
Specific Grant of Access
Access authorization is crucial for securing sensitive data. Beneficiary restricted access, particularly in financial sectors, ensures that designated individuals can view specific information without compromising the overall security framework. For instance, in a healthcare setting, patient records are typically restricted to authorized personnel only, safeguarding personal identifiers and health history. The authorization process must comply with regulations, such as HIPAA in the United States, requiring a detailed documentation of access rights. Furthermore, technology solutions, like role-based access control (RBAC), help in managing permissions efficiently. Proper training on data handling and privacy protocols ensures beneficiaries understand their responsibilities under this restricted access framework.
Defined Scope and Limits
Beneficiary restricted access authorization allows designated individuals to access specific information in a controlled environment. The defined scope includes personal data such as Social Security numbers, bank account details, and medical records relevant to the beneficiary's claims. Limits on this access ensure that only authorized personnel or investigators can view or use this sensitive information, protecting the beneficiary's privacy. This controlled access is typically established through legal frameworks or organizational policies, preventing unauthorized disclosure and ensuring compliance with regulations like the Health Insurance Portability and Accountability Act (HIPAA). Attempts to exceed this scope can lead to serious legal ramifications, and audits might be conducted regularly to maintain compliance.
Security and Confidentiality Terms
Restricted access authorization ensures limited entry to sensitive information. Beneficiaries under this agreement, such as individuals or organizations, must adhere to specific security and confidentiality terms to maintain integrity. These terms may include obligations to protect proprietary data, typically stored on secure servers, and compliance with regulations like the General Data Protection Regulation (GDPR) in the European Union. Unauthorized sharing of access credentials can result in legal repercussions and audits by compliance officers. Furthermore, any breach of confidentiality could lead to substantial financial penalties, undermining trust in the ownership of data. Beneficiaries must commit to ongoing training on cybersecurity practices to mitigate risks associated with information disclosure.
Duration and Termination Conditions
Restricted access authorization for beneficiaries is critical in ensuring that sensitive information remains protected while enabling specific individuals to access necessary data for a defined period. This authorization is often granted for a predetermined duration, typically ranging from six months to one year, depending on the specific requirements of the organization or project. Termination conditions stipulate that access may be revoked if certain criteria are met, such as the conclusion of the designated project, breach of confidentiality agreements, or changes in the beneficiary's status. Additionally, explicit notice periods, such as 30 days, are commonly required before termination to allow for any necessary transitions or data retrieval processes. This structured approach helps maintain data security and compliance with regulatory standards while providing accessible frameworks for authorized users.
Letter Template For Beneficiary Restricted Access Authorization Samples
Letter template of Beneficiary Restricted Access Authorization for Financial Accounts

Letter template of Beneficiary Restricted Access Authorization for Insurance Policies
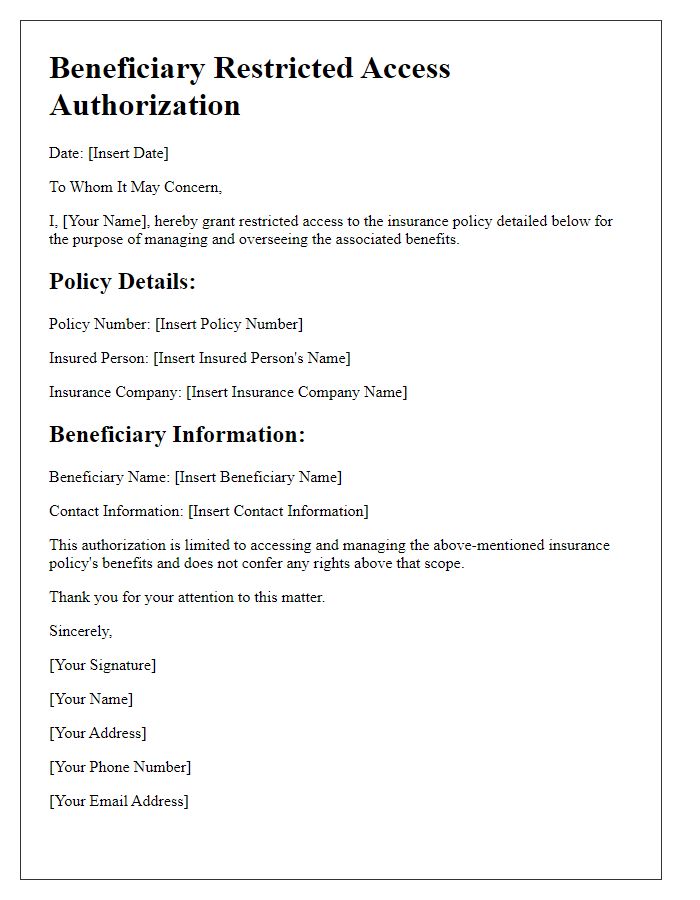
Letter template of Beneficiary Restricted Access Authorization for Trust Funds
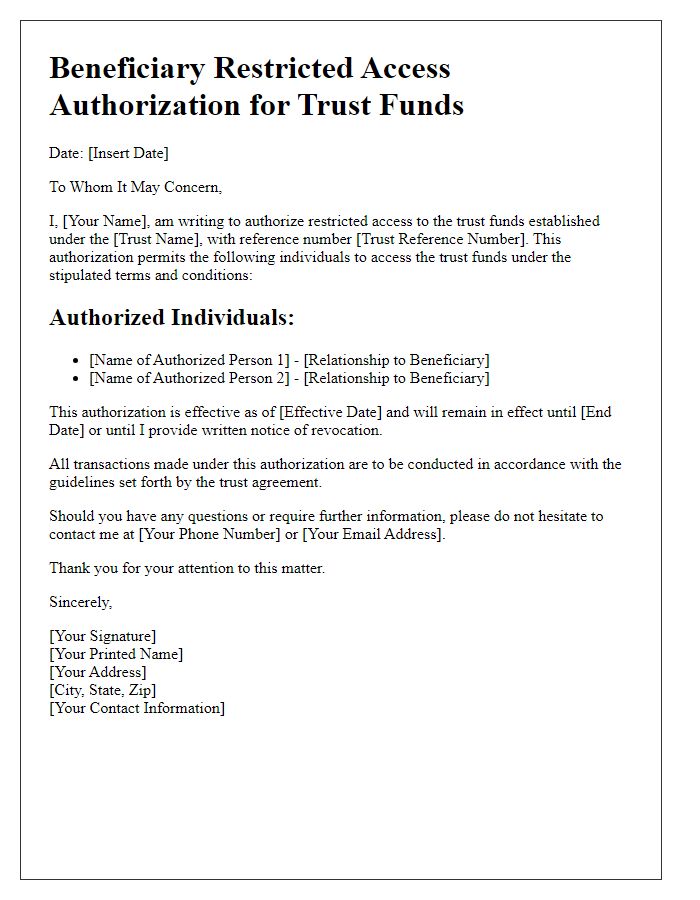
Letter template of Beneficiary Restricted Access Authorization for Retirement Accounts
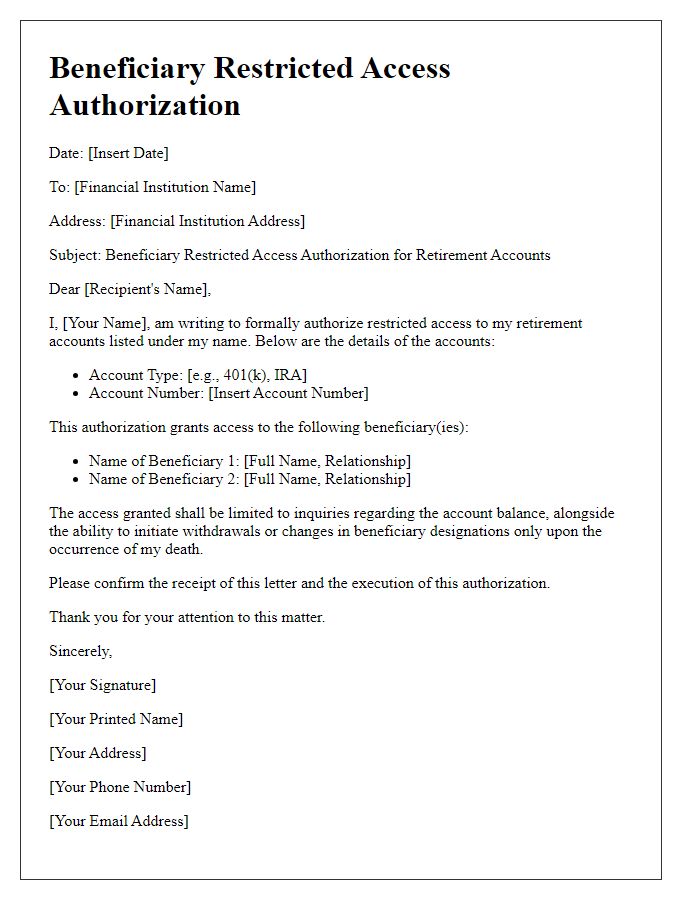
Letter template of Beneficiary Restricted Access Authorization for Real Estate Assets
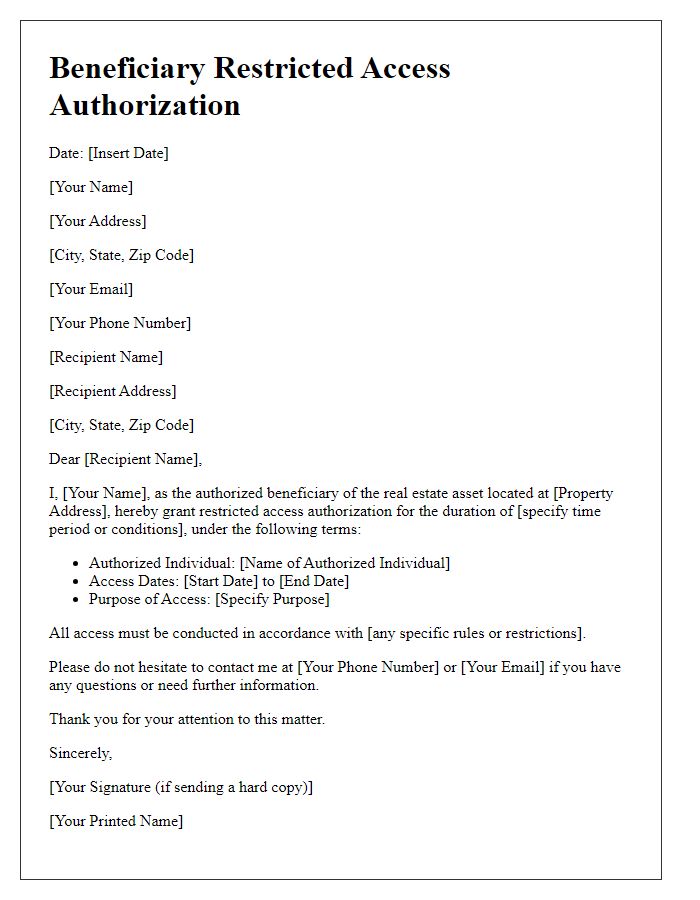
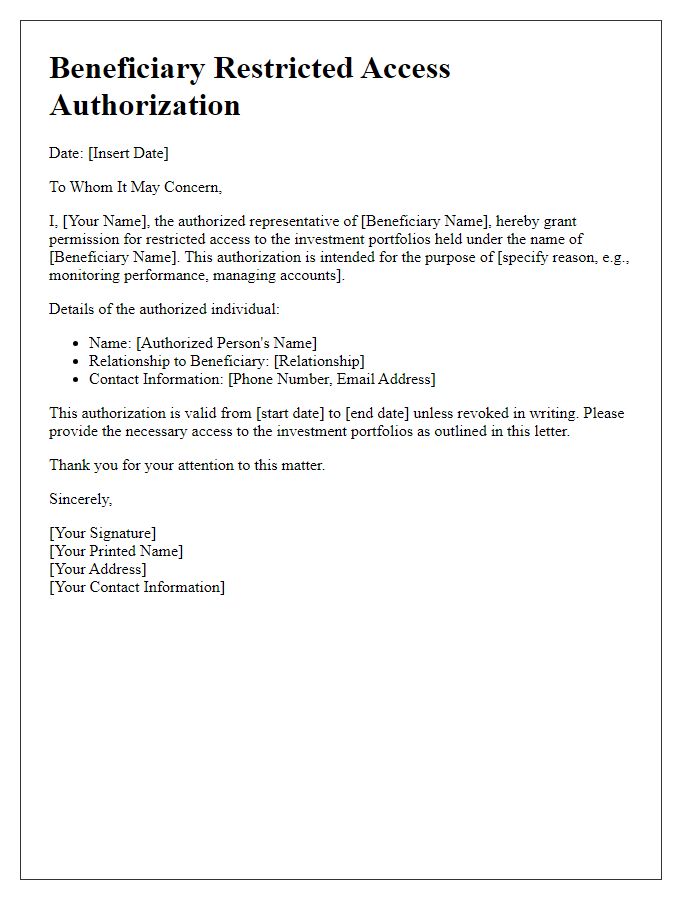
Letter template of Beneficiary Restricted Access Authorization for Investment Portfolios
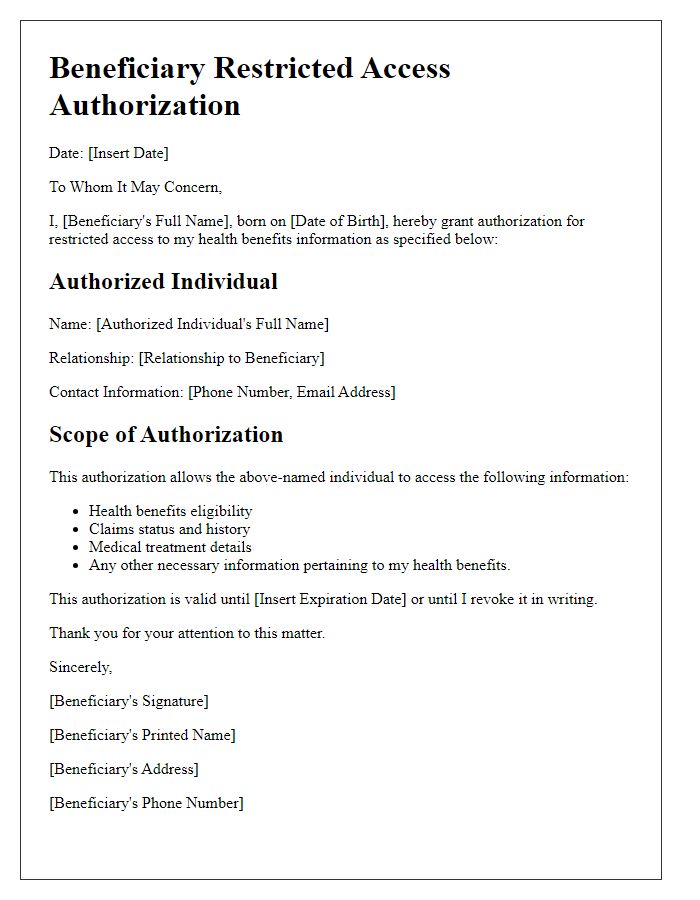
Letter template of Beneficiary Restricted Access Authorization for Health Benefits
Letter template of Beneficiary Restricted Access Authorization for Estate Assets

Letter template of Beneficiary Restricted Access Authorization for College Funds





Comments