In today's digital landscape, securing your online accounts has never been more important, and multi-factor authentication (MFA) is a vital step in protecting your personal information. This article will guide you through the essential MFA guidelines to strengthen your security measures, making it harder for unauthorized access to your accounts. We'll explore various methods of MFA, from SMS verification to authenticator apps, providing you with the knowledge you need to enhance your cyber defenses. Ready to bolster your account security? Read on to discover how to implement MFA effectively!

Security Enhancements
Multi-factor authentication (MFA) serves as a critical security enhancement technique, widely implemented across various sectors to safeguard sensitive data. Organizations like Google and Microsoft utilize MFA to add layers of protection beyond traditional passwords, which can easily be compromised. Typically, MFA incorporates three categories: something you know (password), something you have (a mobile device for authentication codes), and something you are (biometric verification). Research indicates that using MFA can block over 99.9% of automated online attacks. Thus, adopting MFA is imperative for any company, especially in high-stakes environments like financial services or healthcare, where data breaches can result in severe financial and reputational damage.
User Authentication Methods
User authentication methods play a critical role in securing personal data across various platforms, such as online banking and email services. Multi-factor authentication (MFA) enhances security by requiring multiple forms of verification before granting access. Common methods include something the user knows (passwords or PINs), something the user has (security tokens or smartphone authentication apps) and something the user is (fingerprint or facial recognition). MFA significantly reduces the risk of unauthorized access, with studies showing a 99.9% decrease in account compromise when implemented correctly. Following best practices, such as regularly updating authentication methods and being cautious with public Wi-Fi, ensures optimal security for sensitive information across platforms.
Implementation Schedule
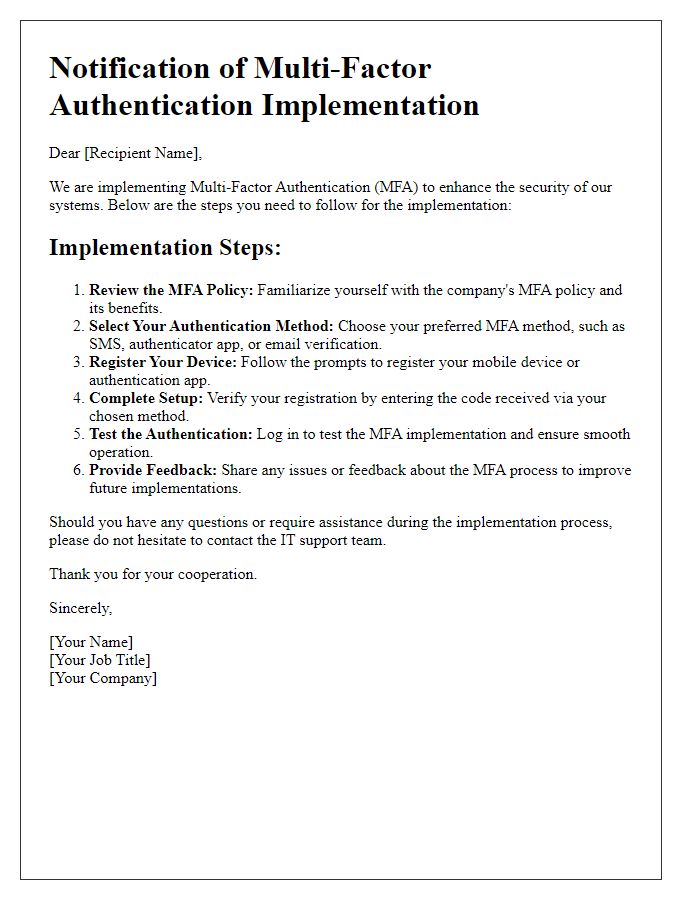
Implementing multi-factor authentication (MFA) is crucial for enhancing security protocols across digital platforms. The implementation schedule consists of four phases over a timeline of three months. Phase one involves assessment and planning, allocating two weeks for evaluation of existing security measures. Phase two encompasses system integration, requiring four weeks for configuring MFA settings on platforms such as Google Workspace and Microsoft 365. Phase three focuses on user training, spanning two weeks to familiarize employees with MFA processes, including methods like SMS verification codes and authenticator apps. Phase four, the deployment phase, initiates a two-week period for rolling out MFA organization-wide, supported by monitoring and feedback collection to ensure efficacy and user compliance post-implementation.
Compliance and Regulations
Multi-factor authentication (MFA) enhances security for organizations, safeguarding sensitive data from unauthorized access. Compliance with regulations such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA) necessitates MFA implementation, ensuring personal information security. MFA typically utilizes three verification methods: something the user knows (passwords), something the user has (security tokens or smartphones), and something the user is (biometric data like fingerprints). The Federal Trade Commission (FTC) recommends MFA as a critical step for businesses to mitigate risks associated with data breaches. Organizations must also keep track of compliance deadlines, ensuring all employees undergo proper training to understand MFA protocols, particularly in high-stakes environments like finance or healthcare. Regular audits can assist in assessing the effectiveness of MFA systems, ensuring adherence to evolving legal standards and protection of user data.
Employee Training and Support
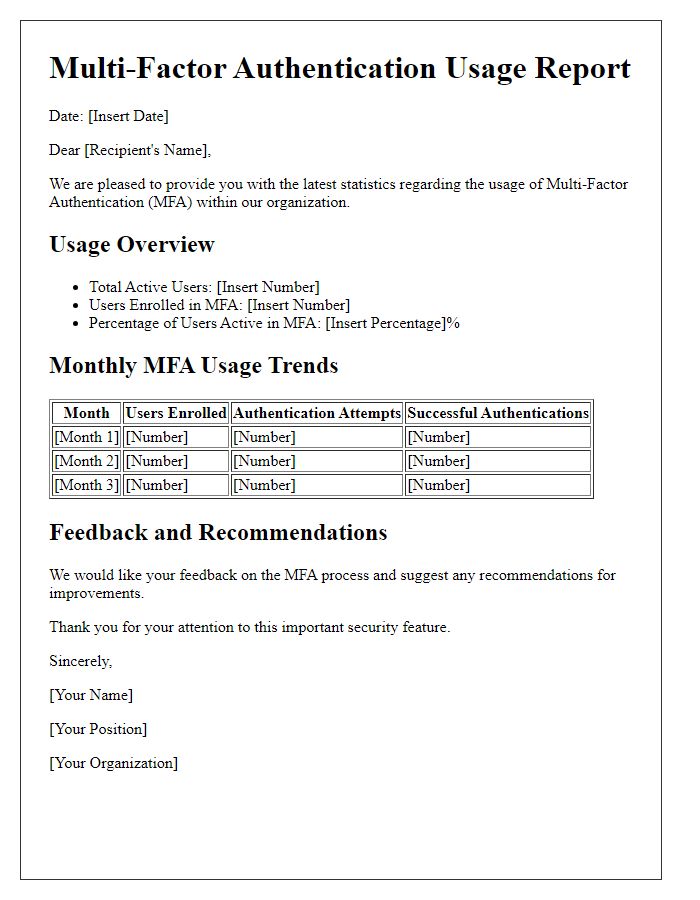
Multi-factor authentication (MFA) significantly enhances security for employee accounts and systems. MFA requires two or more verification factors to gain access, reducing risks of unauthorized access. Common factors include knowledge-based (passwords), possession-based (security tokens), and inherence-based (biometrics). Training sessions, focusing on effective MFA implementation, should be scheduled quarterly to keep employees updated on security protocols. Additionally, ongoing support, such as an easily accessible helpdesk hotline, can assist with troubleshooting authentication issues. Regular audits of access logs and employee compliance will further strengthen the organization's security posture, ensuring that sensitive data remains protected from breaches.











Comments