Hey there, tech enthusiasts! Today, we're diving into the exciting world of bug bounty programs, where companies invite skilled hackers to help uncover vulnerabilities in their software. This collaborative approach not only enhances security but also rewards those who contribute to a safer digital landscape. If you're curious about how these programs work and the benefits they offer to both hackers and organizations alike, keep reading to discover more!

Purpose and Goals
The purpose of a bug bounty program is to identify and mitigate vulnerabilities within software applications, websites, and systems, enhancing overall cybersecurity. Engaging ethical hackers and security researchers allows organizations to gain insights into potential weaknesses before malicious actors exploit them. Goals include fostering a collaborative environment where participants submit findings, rewarding legitimate discoveries with monetary compensation or recognition, and ultimately improving user trust and safety. Notable programs, such as Google's Vulnerability Reward Program (launched in 2010) or Microsoft's Bug Bounty Program (established in 2013), have demonstrated the effectiveness of this proactive approach to security management by significantly reducing risks and patching vulnerabilities efficiently. Implementing a well-structured bug bounty program can also provide invaluable feedback for ongoing software development processes, ensuring robust protection against emerging threats.
Scope of Program
The bug bounty program outlines a comprehensive scope, targeting specific web applications, APIs, and mobile platforms operated by the organization. The eligible domains include primary public websites, such as www.example.com, and associated subdomains, including api.example.com and secure.example.com. Additionally, the scope encompasses mobile applications available on platforms such as iOS (version 14.0 and above) and Android (version 10.0 and above). The program encourages security researchers to identify and report vulnerabilities, including but not limited to, cross-site scripting (XSS) vulnerabilities, SQL injection flaws, and remote code execution exploits. Reports on vulnerabilities affecting unauthorized access to user accounts or sensitive data will be prioritized, with rewards ranging from $100 to $10,000, depending on the severity and potential impact of the identified issues. All participating researchers must adhere to the guidelines outlined in the program to ensure ethical engagement and avoid any disruption to services.
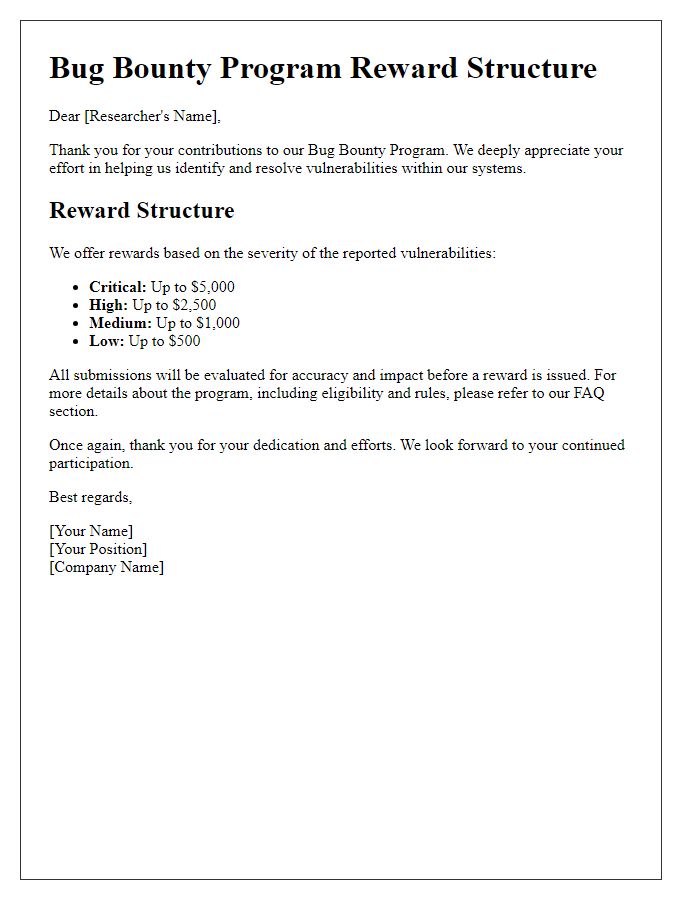
Reward Structure
In bug bounty programs, clear reward structures motivate cybersecurity researchers to identify vulnerabilities within applications and systems. Monetary incentives often range from $100 to $10,000, depending on the severity and impact of the discovered flaw. Critical bugs can earn higher rewards, potentially exceeding $50,000. Well-structured programs may also offer additional bonuses for multiple vulnerabilities found in a single submission. Timely responses and recognition in leaderboards enhance participant engagement. Platforms like HackerOne and Bugcrowd facilitate these interactions, providing secure channels for reporting issues and ensuring accountability. Regular updates on reward tiers and prompt communication contribute to the overall success of these initiatives.
Submission Guidelines
The bug bounty program at XYZ Company encourages ethical hackers to identify vulnerabilities within our web applications, mobile apps, and APIs. Participants must adhere to specific submission guidelines to facilitate efficient reporting. All submissions should include a clear description of the issue, the steps taken to reproduce the vulnerability, and the potential impact on user data or system integrity. Providing screenshots or code snippets can enhance clarity. Reports should focus on critical and high-severity vulnerabilities, identifying issues such as SQL injection or cross-site scripting (XSS) that may endanger our customers' sensitive information. Submissions must be sent via our designated platform, ensuring that confidentiality is maintained throughout the process. We deeply value the contributions from the security community and will compensate findings according to the severity of the vulnerability reported.
Legal Terms and Conditions
A bug bounty program aims to enhance cybersecurity by encouraging ethical hackers to identify vulnerabilities within applications or systems, such as software platforms used by major corporations. Participants, known as researchers, follow legal terms and conditions that outline eligibility, submission guidelines, and reward structures for reporting security flaws. Clear definitions of scope, including specific endpoints, web applications, or network infrastructure, ensure focused testing efforts. Non-disclosure agreements protect sensitive information revealed during the research process. Additionally, the program clearly states prohibited actions, such as testing on live production environments, ensuring safety across impacted platforms. Participants engaging in the bounty program must abide by these legal terms to foster a cooperative relationship between ethical hackers and organizations, ultimately leading to improved digital security.






Comments