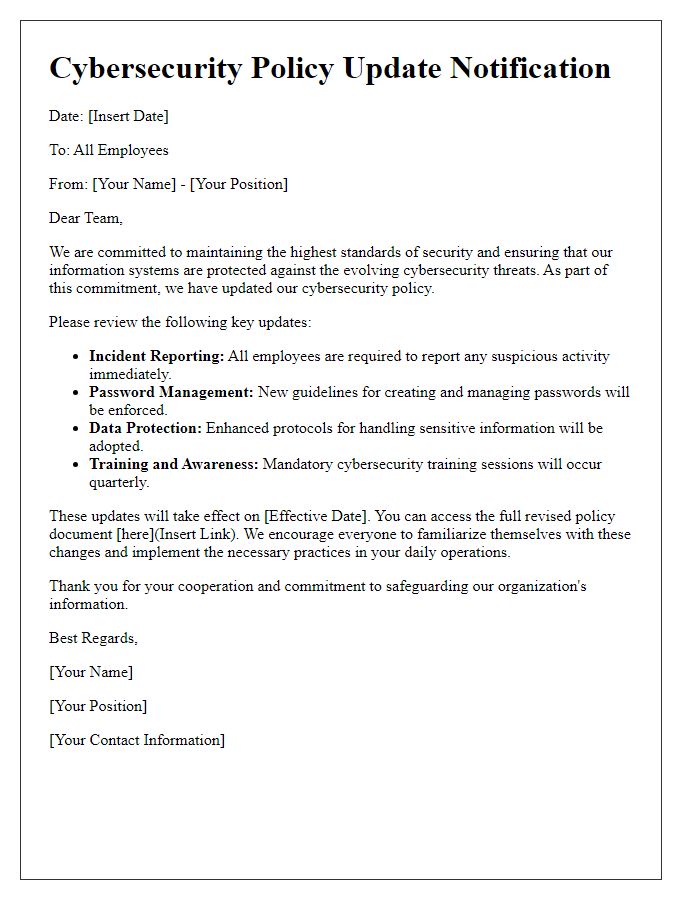
In today's digital age, the importance of a robust cybersecurity policy cannot be overstated. As businesses increasingly rely on technology, safeguarding sensitive information has become a top priority for organizations everywhere. Implementing a comprehensive cybersecurity plan not only protects your assets but also fosters trust among clients and stakeholders. Ready to discover how to effectively implement and adapt a cybersecurity policy in your organization? Read on!

Clear Objectives
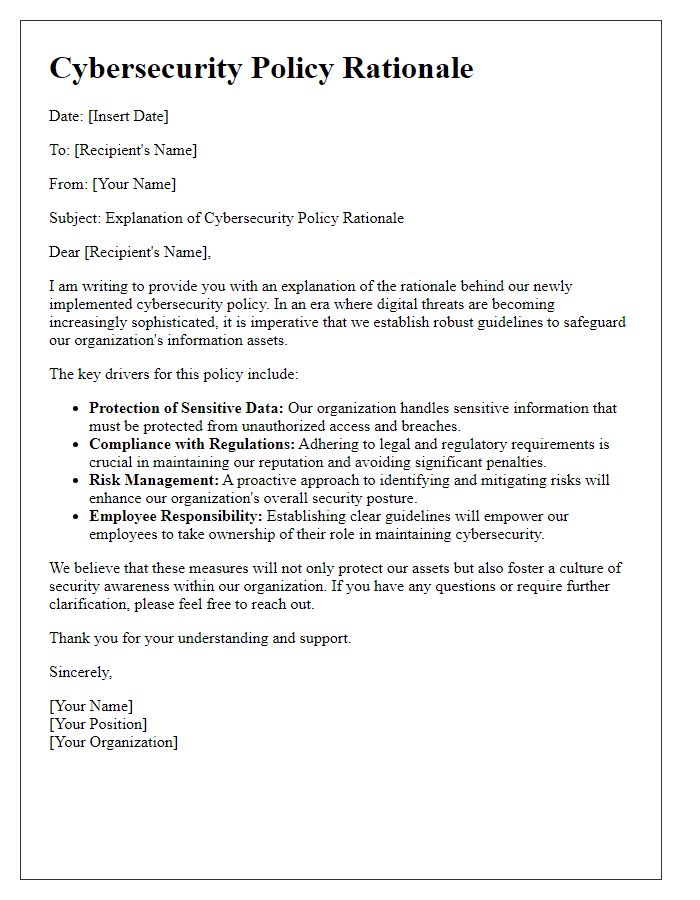
Cybersecurity policy implementation requires well-defined objectives to effectively protect sensitive data and systems within organizations. Establishing clear objectives, such as maintaining data confidentiality, ensuring integrity of information, and promoting availability of systems, empowers teams to focus on specific outcomes. For instance, the objective of reducing data breach incidents by 50% within one year can drive initiatives like employee training programs and system monitoring improvements. Another objective might involve achieving compliance with regulatory frameworks like GDPR (General Data Protection Regulation), which mandates strict data handling practices in the European Union. By setting measurable and attainable goals, organizations can track progress and adapt strategies to meet evolving cybersecurity challenges, such as those posed by increasing cyber threats and sophisticated malware attacks.
Employee Training
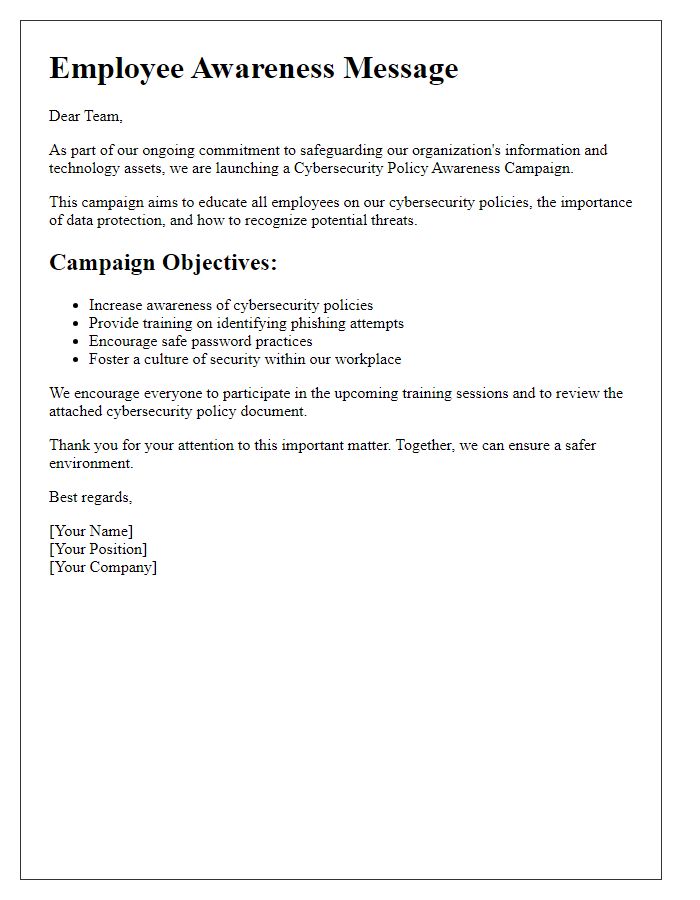
Employee training in cybersecurity is crucial for minimizing risks in an organization. Effective training programs should address key areas such as phishing attacks, password management techniques, and data encryption protocols. Regular workshops, ideally bi-annually, can enhance employees' understanding of potential threats and safe online practices. Organizations can utilize simulations, such as mock phishing emails, to assess employee awareness and response to security breaches. Additionally, incorporating industry-standard certifications, such as CompTIA Security+ or Certified Information Systems Security Professional (CISSP), into the training curriculum can further elevate the organization's security posture. Continuous learning initiatives can ensure that employees remain informed about the latest cybersecurity trends and tactics used by malicious actors around the world.
Risk Assessment
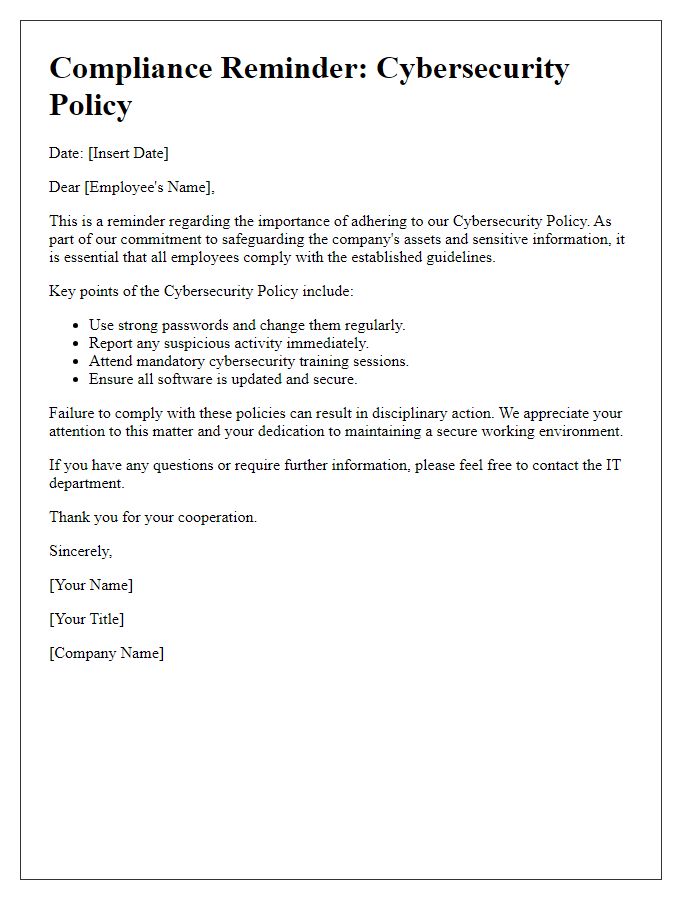
Risk assessment plays a crucial role in the cybersecurity policy implementation process for organizations. A comprehensive risk assessment identifies potential vulnerabilities and threats (like phishing attacks, malware, data breaches) that can impact sensitive data and systems, such as customer information databases and financial transaction systems. By evaluating various risk factors (like likelihood of occurrence and potential impact), businesses can prioritize their cybersecurity measures and allocate resources effectively. The assessment often utilizes frameworks like NIST (National Institute of Standards and Technology) or ISO/IEC 27001 to establish a systematic approach. Additionally, awareness of regulatory compliance (such as GDPR for European Union citizens or HIPAA for healthcare information in the United States) is essential to ensure that the organization meets legal requirements in protecting sensitive data. By conducting regular risk assessments, organizations can adapt to emerging threats in the digital landscape, ensuring a robust cybersecurity posture.
Incident Response Plan
In today's digital landscape, an effective Incident Response Plan (IRP) is essential for organizations, such as corporations in the finance sector or healthcare institutions. An IRP is a structured approach to managing cyber incidents (like data breaches or ransomware attacks), ensuring that threats are mitigated swiftly and efficiently. Key components include preparation (such as employee training and resource allocation), detection (using advanced security monitoring tools to identify suspicious activity), analysis (assessment of incident severity), containment (isolating affected systems to prevent further damage), eradication (removing threats), recovery (restoring systems and operations), and post-incident review (learning and improving based on experiences). Successful IRP implementation can significantly reduce downtime and financial loss caused by cyber threats, with organizations potentially avoiding millions in damages, depending on the severity of the incident.
Continuous Monitoring
Continuous monitoring is essential for maintaining robust cybersecurity, especially in environments with sensitive data. This process involves ongoing assessment of security controls and threat landscapes across systems and networks. Advanced tools and technologies, such as Security Information and Event Management (SIEM) systems, enable organizations to collect and analyze security events in real-time. Monitoring must encompass all endpoints, including servers and workstations, as well as cloud services, to ensure comprehensive risk management. Regular audits, such as vulnerability assessments and penetration tests, should complement continuous monitoring efforts. By consistently tracking metrics like unauthorized access attempts or unusual network behavior, organizations can proactively address emerging threats and enhance their overall security posture.









Comments