In today's fast-paced digital world, staying informed about telecommunication security is crucial for both businesses and individuals. Whether you're a tech enthusiast or simply someone who values privacy, understanding the latest updates can help protect your information and ensure seamless communication. With recent advancements and growing threats, it's important to keep abreast of the developments in this ever-evolving landscape. So, grab a cup of coffee and join us as we dive deeper into the essential updates and strategies for enhancing your telecommunication security.

Purpose of the Security Update
The purpose of the telecommunication security update focuses on enhancing the protection of sensitive user information across networks. This update aims to address vulnerabilities identified in recent assessments, including risks associated with outdated encryption protocols and potential data breaches. Improved security measures, such as advanced authentication methods and real-time threat detection systems, will be implemented to protect user data from unauthorized access. Additionally, compliance with regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) will be ensured, safeguarding user privacy and promoting trust in telecommunication services. The update is critical for maintaining network integrity and preventing service disruptions caused by cyber threats.
New Security Features and Enhancements
Telecommunication networks face increasing security threats, prompting the implementation of new security features and enhancements. Advanced encryption protocols (like AES-256, which offers robust protection) will be deployed to safeguard data transmission across mobile and broadband services. Multi-factor authentication (MFA) methods will strengthen user access protocols, requiring multiple verification steps before granting access to sensitive account information. Regular security audits will be conducted to identify vulnerabilities and ensure compliance with telecommunications regulations, improving overall network integrity. Additionally, artificial intelligence (AI) systems will monitor traffic patterns in real-time, detecting and mitigating potential threats before they impact service quality. These updates aim to enhance user confidence and maintain the security of telecommunications infrastructures against evolving cyber threats.
User Impact and Required Actions
Telecommunication security updates are critical for maintaining the integrity of user data and ensuring seamless connectivity. Recent vulnerabilities identified within network protocols (like SS7 exploitation) have potential impacts on user privacy, particularly in regions with high mobile penetration, such as Southeast Asia, where nearly 500 million mobile users rely on cellular networks. Service disruptions can arise from unauthorized access, leading to service downtime and data breaches. Users must implement two-factor authentication (2FA) across platforms to enhance security. Additionally, updating device firmware is crucial; manufacturers recommend checking for updates at least bi-monthly. Awareness of phishing tactics, especially with SMS, is vital as cybercriminals target users in both urban and rural areas.
Compliance with Industry Standards
Telecommunication security updates play a crucial role in ensuring compliance with industry standards, such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework. These standards outline essential practices for protecting sensitive data within telecommunications systems. Organizations must regularly assess their security protocols to fulfill requirements established by regulatory entities like the Federal Communications Commission (FCC). Compliance audits may reveal vulnerabilities in systems, necessitating immediate updates or enhancements. Implementing best practices, including encryption technologies and intrusion detection systems, creates a robust defense against cyber threats. Training employees on security awareness further bolsters resilience against social engineering attacks, crucial for maintaining customer trust in services provided. As technology evolves, staying up-to-date with compliance measures is vital for protecting customer information from breaches.
Contact Information for Support and Inquiries
In the evolving landscape of telecommunication security, it is vital for users to stay informed about potential vulnerabilities and the measures taken to safeguard communication networks. Key elements include regular updates regarding encryption protocols, firewall enhancements, and compliance with industry standards such as the General Data Protection Regulation (GDPR). Stakeholders should be aware of designated contact points for support and inquiries, typically accessible through official channels, often available 24/7 to address concerns. These lines of communication are critical for reporting suspicious activities, accessing security patches, and understanding changes in privacy policies. Organizations may also conduct periodic training sessions, webinars, or informational newsletters to keep users educated on emerging threats and best practices.
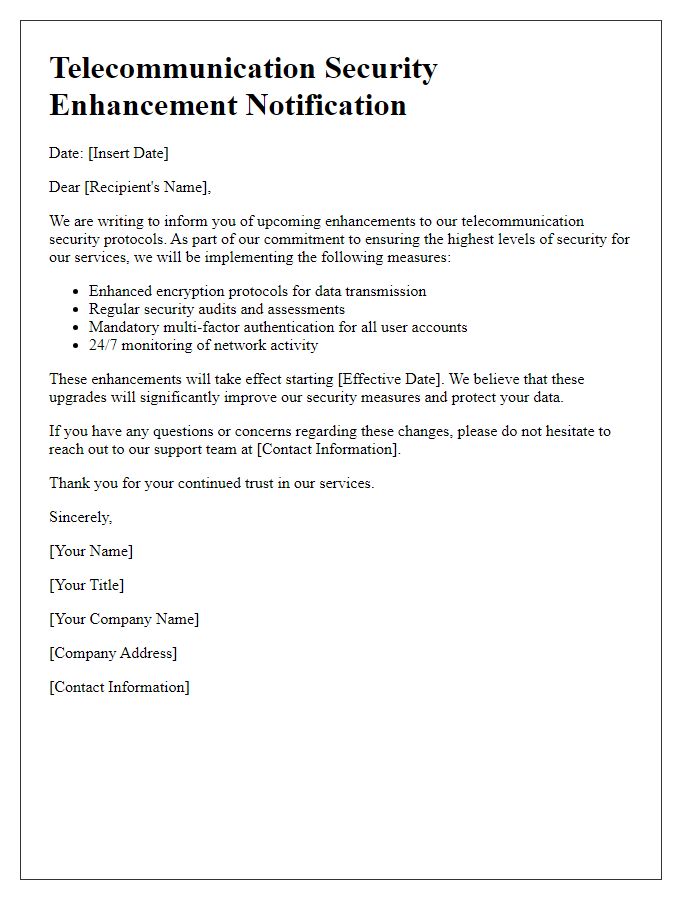
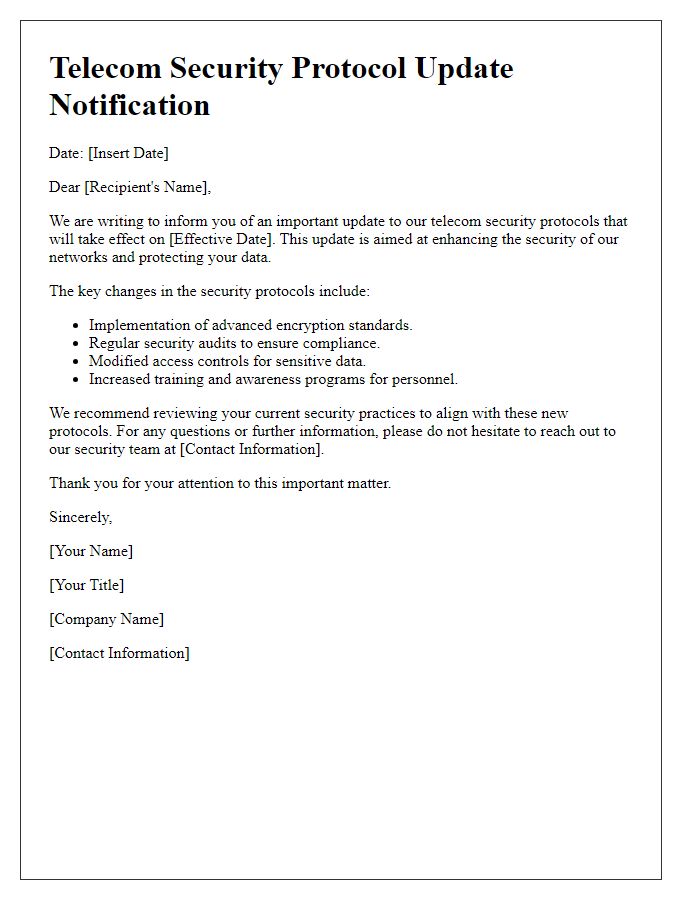
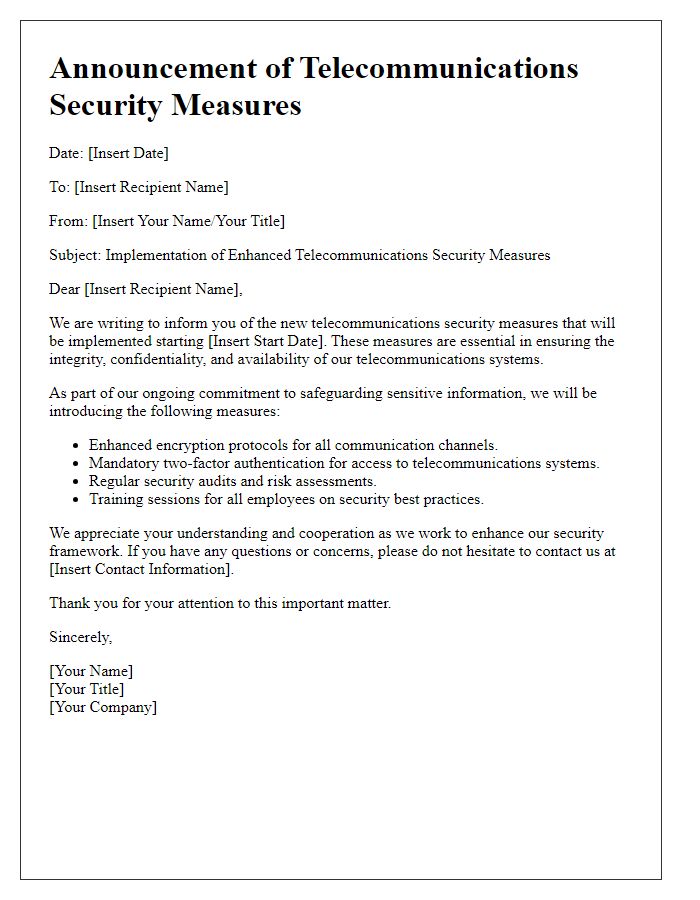
Letter Template For Telecommunication Security Update Samples
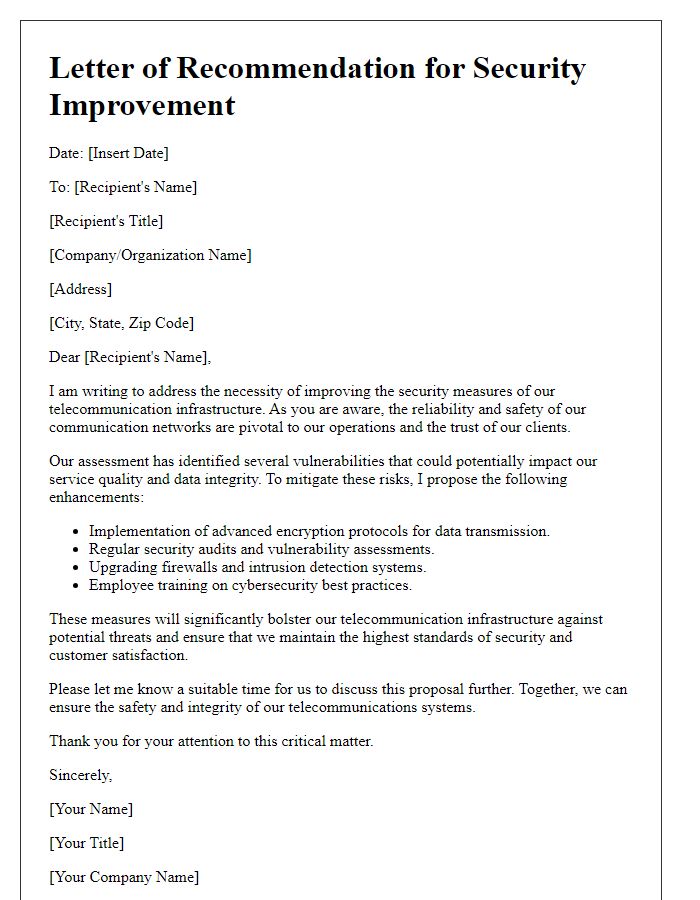
Letter template of telecommunication infrastructure security improvement




Comments