In today's fast-paced digital landscape, forming secure technology partnerships is more crucial than ever for businesses aiming to stay ahead. By collaborating with trusted partners, organizations can innovate more effectively and shield their assets from potential cyber threats. It's all about leveraging collective strengths while ensuring data protection and compliance. Ready to dive deeper into this essential topic? Let's explore how a well-structured partnership agreement can pave the way for a successful and secure collaboration!

Introduction and Agreement Purpose
A secure technology partnership agreement aims to establish a collaborative framework between organizations focused on leveraging advanced technology solutions. This agreement outlines the mutual goals of enhancing cybersecurity measures and fostering innovation across systems. By defining roles, responsibilities, and expectations, this partnership seeks to create a robust environment for sharing resources and knowledge while protecting sensitive data from potential threats. Ensuring compliance with regulatory standards, such as General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), forms a crucial aspect of this partnership, safeguarding both parties' interests and promoting trust. In addition, the agreement addresses intellectual property rights and confidentiality protocols to secure proprietary information throughout the collaboration process.
Confidentiality and Data Protection
In a secure technology partnership agreement, confidentiality and data protection are paramount to ensuring that sensitive information remains protected. Organizations, such as TechCorp and Innovate Solutions, collaborate to develop cutting-edge software applications while adhering to stringent data protection regulations, like the General Data Protection Regulation (GDPR) enforced across the European Union. Each party commits to limiting data access to authorized personnel only, using strong encryption methods for data storage, and regularly updating cybersecurity protocols to mitigate risks. In the event of a data breach, the affected party must notify the other party within 72 hours, as mandated by GDPR guidelines, ensuring prompt action is taken to safeguard user information. This agreement also outlines the procedures for data handling, including deletion and transfer processes, to maintain compliance with legal requirements and protect intellectual property throughout the partnership's duration.
Roles and Responsibilities
A secure technology partnership agreement outlines the roles and responsibilities between collaborating entities within a technological framework. The agreement specifies the responsibilities of each partner, including data protection protocols, software development guidelines, and system maintenance duties. Defined roles such as administrator, developer, and compliance officer ensure that all security measures align with industry standards such as ISO/IEC 27001. Partners must adhere to regular security audits and vulnerability assessments to maintain secure operations. Additionally, clear communication channels, reporting structures, and incident response plans must be established to streamline cooperation and address any potential breaches efficiently. Legal obligations pertaining to intellectual property and confidential information, including trade secrets and proprietary technology, must also be underlined within the agreement to safeguard all parties' interests.
Intellectual Property Rights
Intellectual Property Rights (IPR) are crucial in establishing the framework for secure technology partnership agreements. Clearly defined IPR outlines the ownership and usage rights of proprietary technologies and innovations between companies, impacting their competitive advantages. In this context, patents (legal protections for inventions), copyrights (protections for original works of authorship), and trademarks (identifications of source of goods or services) play significant roles. The agreement must address the scope of use for intellectual property, including any licensing agreements and restrictions on disclosure. Additionally, clauses regarding joint developments, modifications, and dispute resolution mechanisms are essential. Such agreements ensure that both parties maintain their competitive edge and foster a mutually beneficial partnership. The enforcement of confidentiality provisions is also essential, preventing unauthorized use or distribution of proprietary information during and after the partnership.
Termination and Liability
Termination of a secure technology partnership agreement can occur under specific circumstances, including breach of contract, insolvency, or mutual consent. The parties, such as Company A and Company B, must provide written notice at least 30 days in advance before termination takes effect. Liability clauses should clearly outline responsibilities in case of data breaches or failures in security protocols, potentially imposing limits on damages to actual losses incurred, excluding indirect or consequential damages. Additionally, jurisdictions like California or New York may have unique regulations that influence liability and termination processes, highlighting the importance of legal review before finalization. Compliance with applicable laws, such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA), must also be maintained throughout the partnership.
Letter Template For Secure Technology Partnership Agreement Samples
Letter template of secure technology partnership agreement for data sharing.

Letter template of secure technology partnership agreement for joint development.

Letter template of secure technology partnership agreement for software integration.

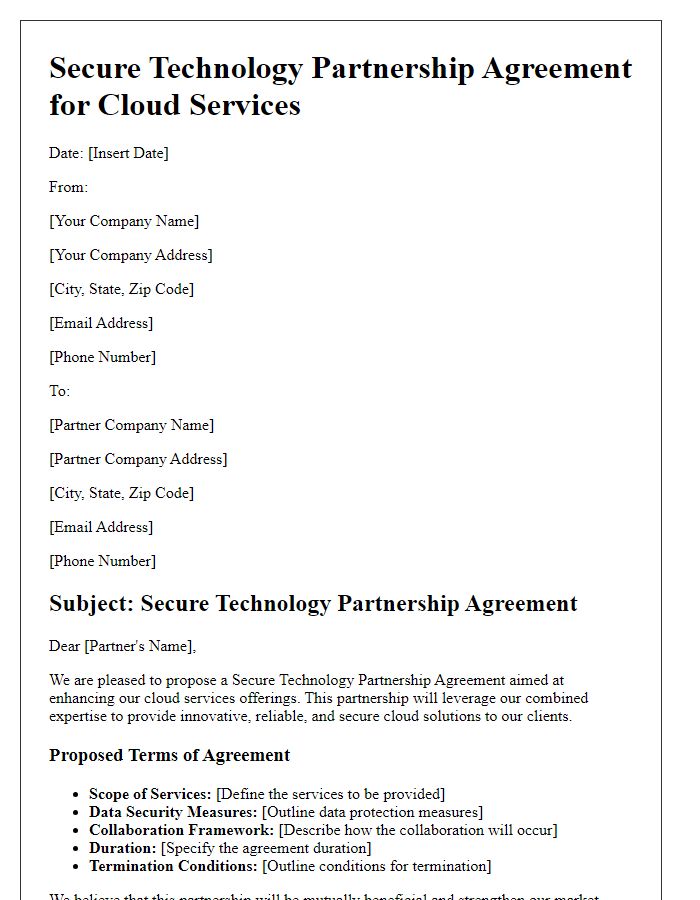
Letter template of secure technology partnership agreement for cloud services.
Letter template of secure technology partnership agreement for cybersecurity collaboration.

Letter template of secure technology partnership agreement for hardware innovation.

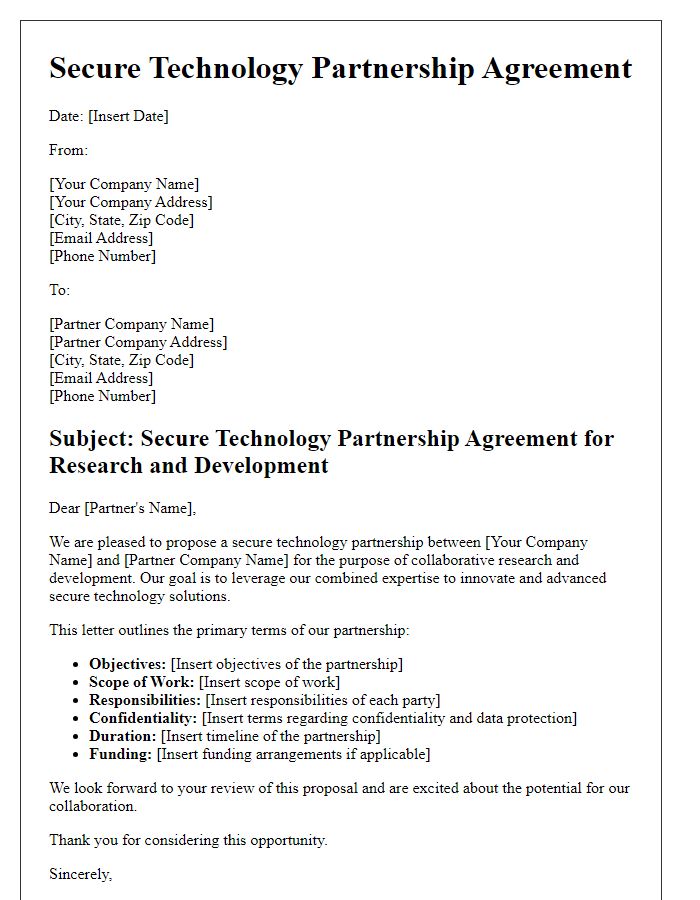
Letter template of secure technology partnership agreement for research and development.
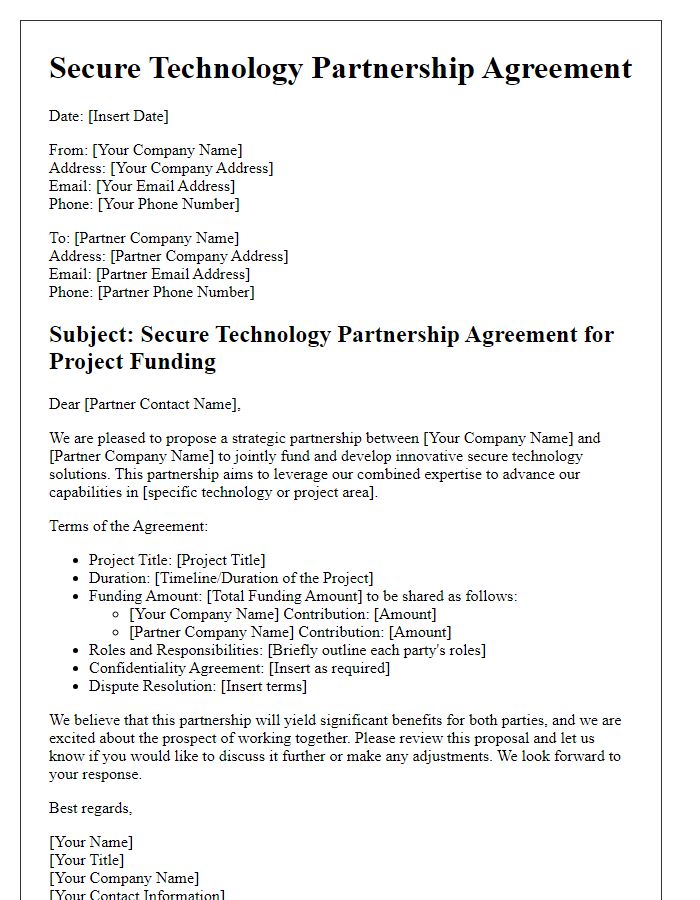
Letter template of secure technology partnership agreement for project funding.
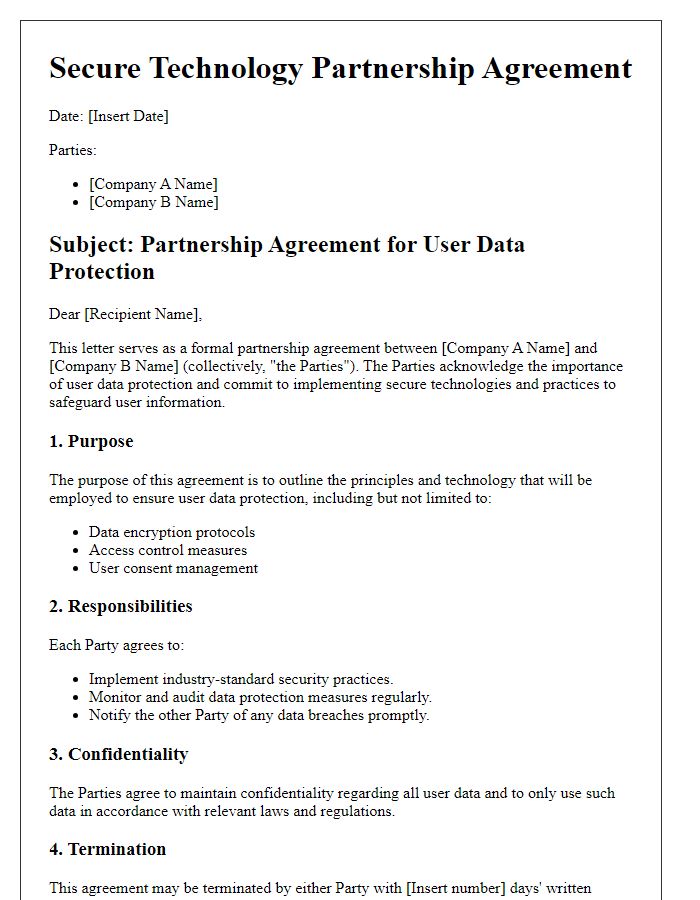
Letter template of secure technology partnership agreement for user data protection.



Comments