In today's increasingly digital world, ensuring the security of your technology systems is more important than ever. With cyber threats evolving at a rapid pace, having a comprehensive security checklist can help safeguard your sensitive information and maintain operational integrity. This article will guide you through a practical template that covers all essential security measures you should consider implementing. So, let's dive in and explore how to fortify your tech defenses!

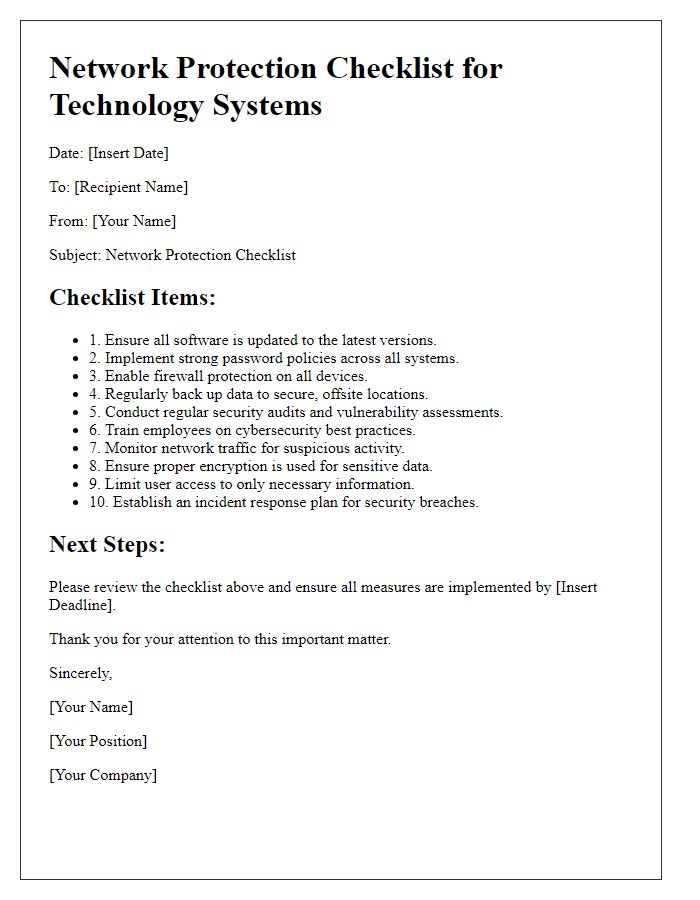
System Access Control
The security of System Access Control is critical in safeguarding sensitive information within technological environments, particularly in organizational settings like corporate offices and healthcare facilities. Effective access control mechanisms include multifactor authentication (MFA), which combines passwords with biometric verification methods, such as fingerprint or facial recognition. Regular audits (quarterly or biannually) of access logs can help identify unauthorized access attempts, alerting security personnel to potential breaches. Role-based access control (RBAC) ensures that personnel, such as IT staff or finance department employees, only have access to data necessary for their roles, complying with regulations like General Data Protection Regulation (GDPR). Implementing time-bound access, such as temporary access during specific projects, also enhances security measures. Additionally, employee training programs on recognizing phishing attacks are essential, as human error often leads to security vulnerabilities.
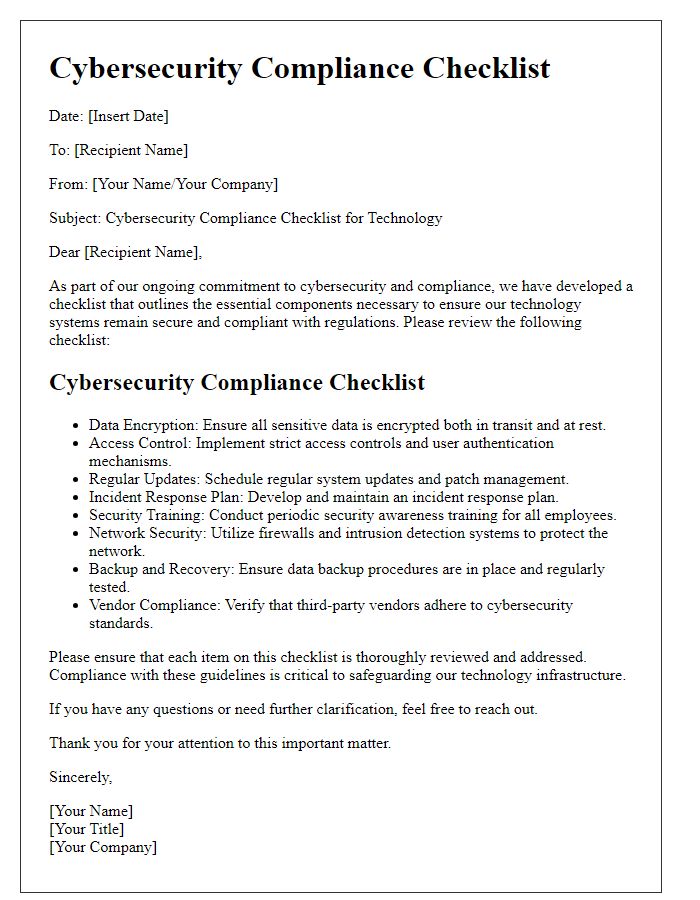
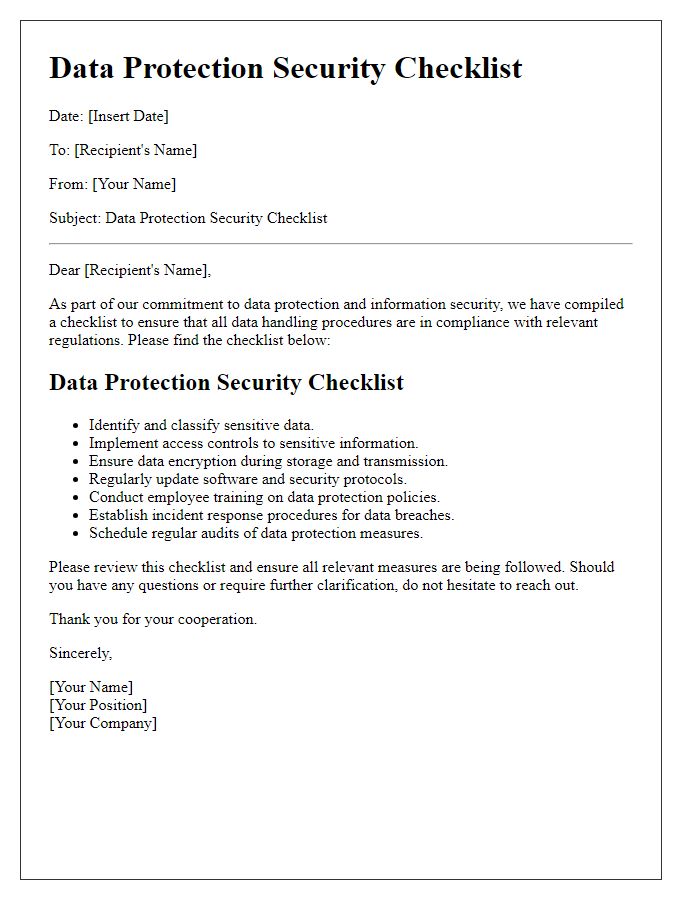
Data Protection Measures
Implementing robust data protection measures is essential for safeguarding sensitive information across technology systems. Encryption techniques, such as AES (Advanced Encryption Standard) with 256-bit keys, ensure data privacy during transmission and storage. Regular security audits, ideally conducted quarterly, can identify vulnerabilities in systems and processes, promoting timely remediation. User access controls, including role-based access and multi-factor authentication (MFA), can limit unauthorized access to critical data. Additionally, data backup solutions should be in place, with backups occurring daily and stored both onsite and offsite to prevent data loss from ransomware attacks or natural disasters. Employee training programs focusing on cybersecurity awareness are necessary to educate staff about phishing scams and safe handling of sensitive information. Comprehensive incident response plans, outlining clear procedures for data breaches, must be established to minimize potential damage.
Incident Response Procedures
The Incident Response Procedures are crucial for ensuring organizational security in technology systems. These steps outline a structured approach to managing security incidents effectively, minimizing damage. Initial preparation should include a well-defined incident response team composed of cybersecurity professionals, network administrators, and legal advisors. This team's roles and responsibilities must be clearly defined, ensuring a swift response. Detection methods, including automated monitoring tools and manual threat analysis, should be established to identify potential breaches early. Once an incident is confirmed, containment strategies must be deployed promptly to limit exposure, such as isolating affected systems. The next phase involves eradication, ensuring that the root cause of the incident is identified and removed from the environment, including malware removal and patching vulnerabilities. Post-incident, a thorough analysis should be conducted to evaluate the effectiveness of the response and identify areas for improvement, followed by detailed documentation of the incident for compliance and auditing purposes. Regular training exercises must be incorporated to keep team members prepared for real-life incidents.
Regular Security Audits
Regular security audits are essential for safeguarding technology systems against potential vulnerabilities and threats. Organizations must conduct these assessments at least biannually to identify security gaps within their network infrastructure. Key components include reviewing firewall configurations, evaluating access controls for sensitive data, and analyzing intrusion detection systems. Performing audits against standards such as the National Institute of Standards and Technology (NIST) guidelines will help ensure compliance and enhance overall security posture. Additionally, documenting findings in detailed reports facilitates tracking of remediation efforts and updates to security protocols. Implementing a robust audit process minimizes risks of unauthorized access and data breaches, protecting valuable information assets in corporate environments.
Employee Security Training
Employee security training programs are essential for safeguarding organizational technology systems against potential threats. Effective training typically includes modules on identifying phishing scams, understanding the importance of strong passwords, and recognizing social engineering tactics. Regular refresher courses (at least quarterly) help reinforce learned concepts. Implementing interactive elements, such as simulated cyber-attack scenarios, enhances engagement and retention. Utilizing a Learning Management System (LMS) can streamline tracking of employee progress and compliance. An effective program may also incorporate role-specific training to address unique risks associated with various job functions. Ultimately, well-informed employees serve as the first line of defense in maintaining robust security protocols across company networks.










Comments