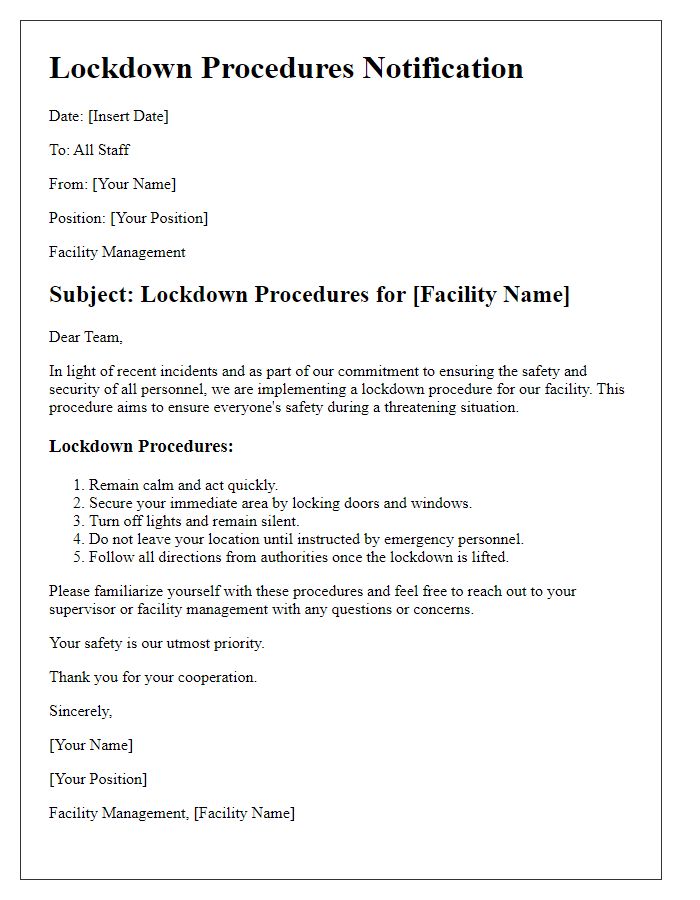
In today's world, ensuring the safety and security of our spaces is more important than ever. Establishing secure entry procedures not only protects our premises but also fosters a sense of trust and belonging among our community. By implementing clear guidelines and protocols, we can create an environment where everyone feels safe and valued. Curious about how to effectively set up these procedures? Read on!

Clear Identification Process
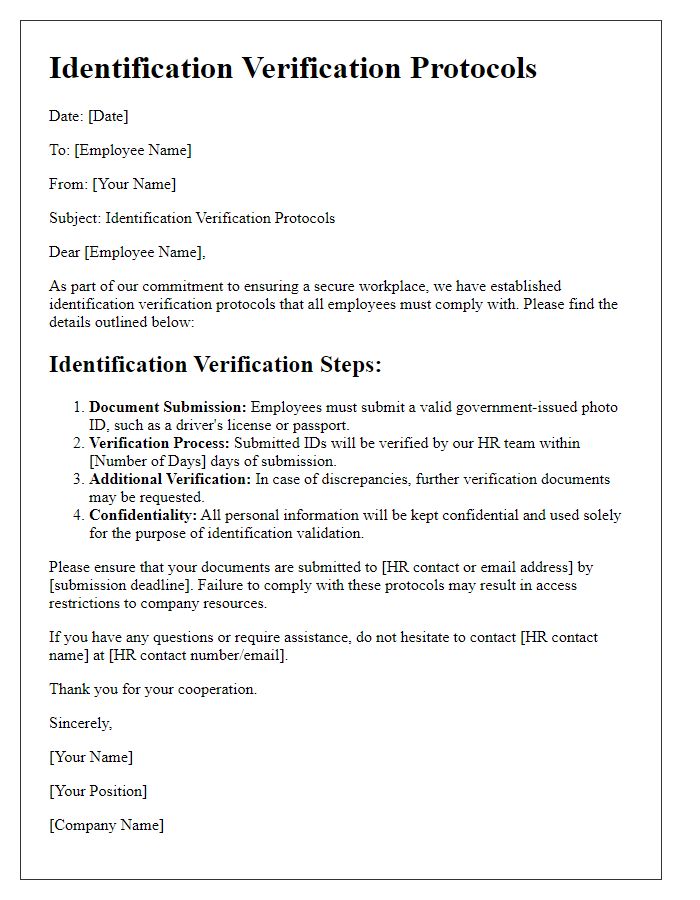
Secure entry procedures require a clear identification process to ensure safety and access control, particularly in sensitive environments like corporate offices and government facilities. Each individual seeking entry must present valid identification, such as a government-issued photo ID (e.g., driver's license, passport) confirming identity and eligibility. Staff members must verify these credentials against access control lists, which should be updated regularly, emphasizing a systematic approach. The identification process may also include biometric verification methods, like fingerprint scanning or facial recognition technology, enhancing security measures. Additionally, the entry point should be monitored by surveillance systems to record and review access activities, deterring unauthorized access and ensuring accountability.
Efficient Access Control
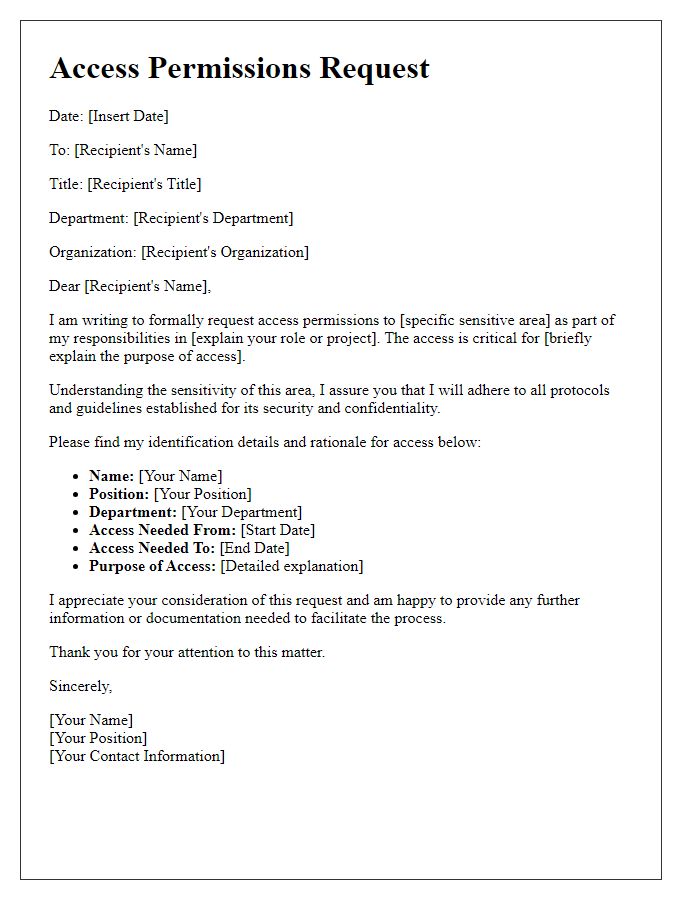
Efficient access control systems play a crucial role in enhancing security at facilities, particularly in high-threat environments such as corporate offices and data centers. Key elements include biometric scanners, like fingerprint recognition or iris scanning, capable of accurately identifying individuals within seconds. Modern access control systems, utilizing RFID technology, allow employees to swipe access cards (typically encoded with a unique identification number) to gain entry, streamlining the entry process while maintaining security integrity. Integration with CCTV surveillance systems ensures real-time monitoring and recording of access events, providing a comprehensive overview of secure areas. Additionally, periodic audits of access logs, which may include timestamps and user details, help identify irregular patterns and enforce compliance with security policies.
Secure Communication Protocols
Secure communication protocols are essential for maintaining the integrity and confidentiality of data transmitted over networks. Examples include HTTPS (Hypertext Transfer Protocol Secure), which encrypts data between web browsers and servers, safeguarding sensitive information. In addition, protocols such as TLS (Transport Layer Security) enhance security during data exchange, crucial for online transactions and communications. Secure entry procedures often utilize these protocols to authenticate users, ensuring that only authorized individuals access sensitive information or systems, particularly in environments like financial institutions or healthcare facilities. Understanding and implementing these protocols helps mitigate risks associated with data breaches and cyber threats.
Regular System Audits
Regular system audits enhance the security framework of organizations by ensuring compliance with established protocols and identifying vulnerabilities. These audits involve comprehensive assessments of network systems, data integrity, software applications, and user access controls, typically conducted quarterly to align with industry standards like ISO 27001. Key components analyzed during audits include intrusion detection systems, log management practices, and data retention policies, highlighting potential risks related to unauthorized access or data breaches. Organizations in critical sectors such as finance or healthcare often implement these protocols to safeguard sensitive information and maintain operational efficiency. Auditor reports summarize findings and recommend improvements, leading to informed decision-making and stronger security postures.
Employee Training and Awareness
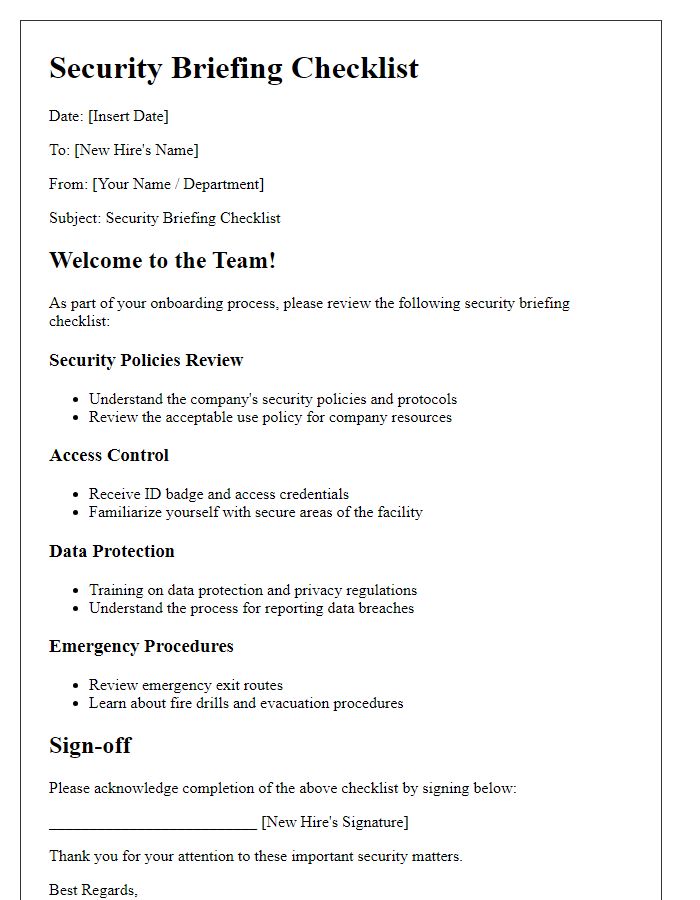
Secure entry procedures are essential for maintaining the safety of organizational premises, particularly in corporate settings. Training programs emphasize the importance of access control systems, such as biometric scanners and RFID card readers, commonly utilized in office buildings across metropolitan areas. Employees, numbering thousands in large corporations, receive instruction on recognizing unauthorized access, implementing visitor protocols, and reporting suspicious behavior to security personnel. Awareness campaigns utilize posters and digital communications, enhancing understanding of the impact of security breaches, with case studies detailing events like the 2017 data breach affecting Equifax, which compromised sensitive information of 147 million individuals. Continuous reinforcement through drills and updates ensures that employees remain vigilant and informed about the latest security trends and technologies.





Comments